Microsoft 365 Copilot – Environment Configuration and Compliance Enforcement
Microsoft 365 Copilot – Environment Configuration and Compliance Enforcement
Overview
This document outlines the configuration steps taken to prepare our Microsoft 365 environment for Copilot integration. It includes sensitivity label enforcement, Intune deployment, Conditional Access policies, and enterprise search connector setup. All actions were performed in alignment with project directives and compliance requirements.
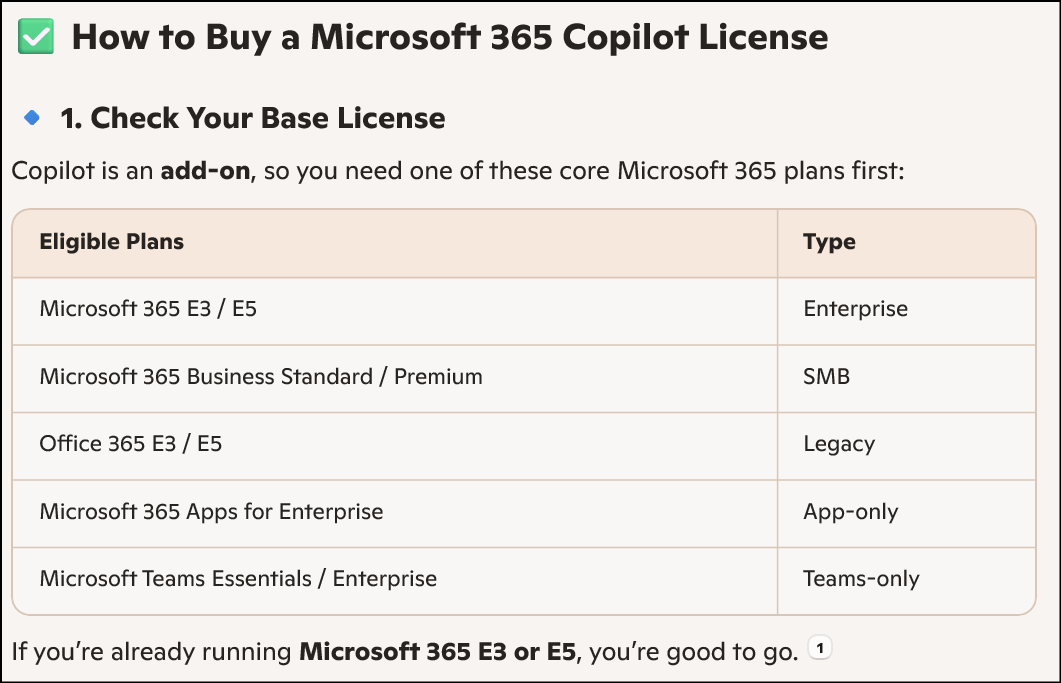 1. Go to https://admin.exchange.microsoft.com
1. Go to https://admin.exchange.microsoft.com
Create a Mail Enabled Group “copilotUsers”

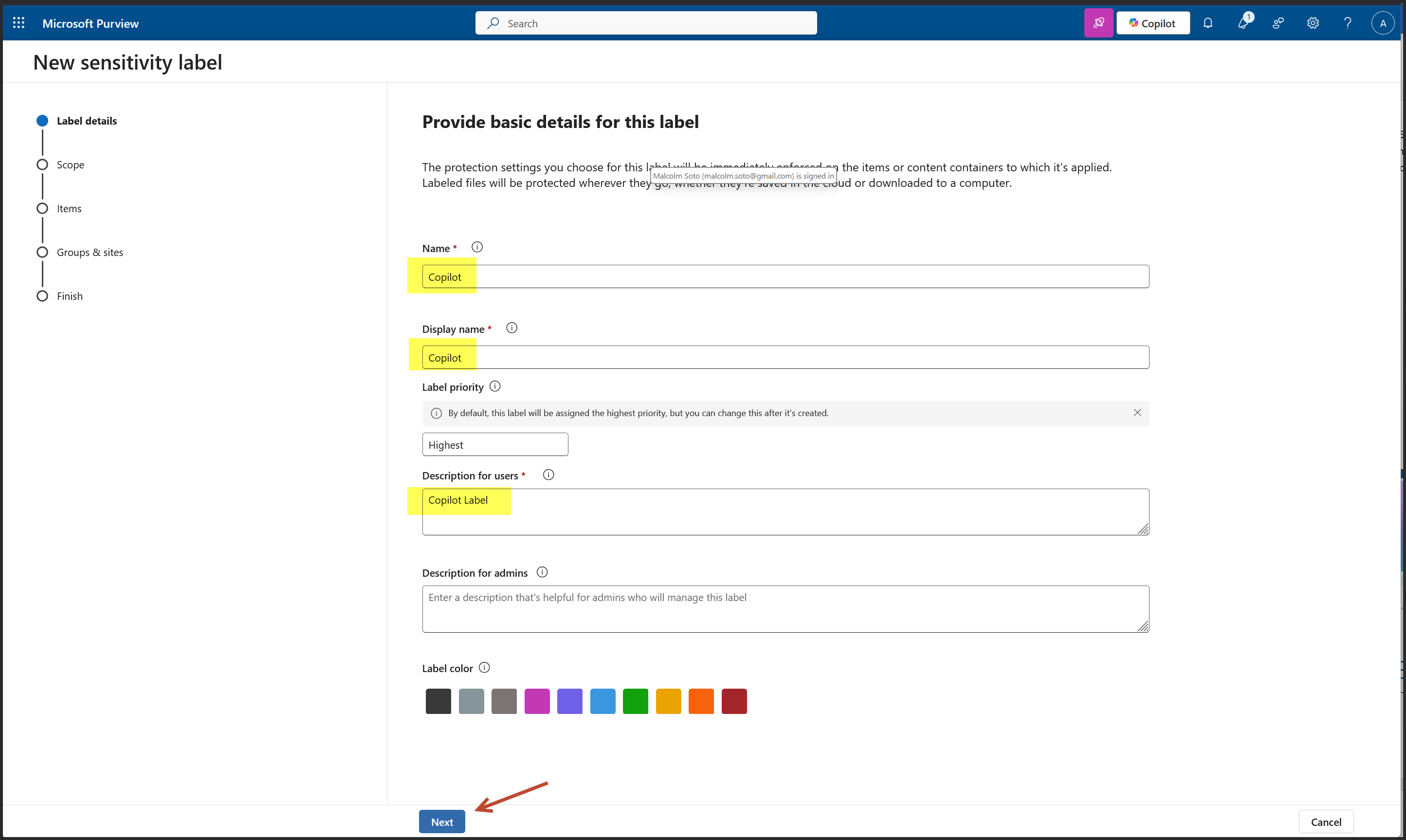
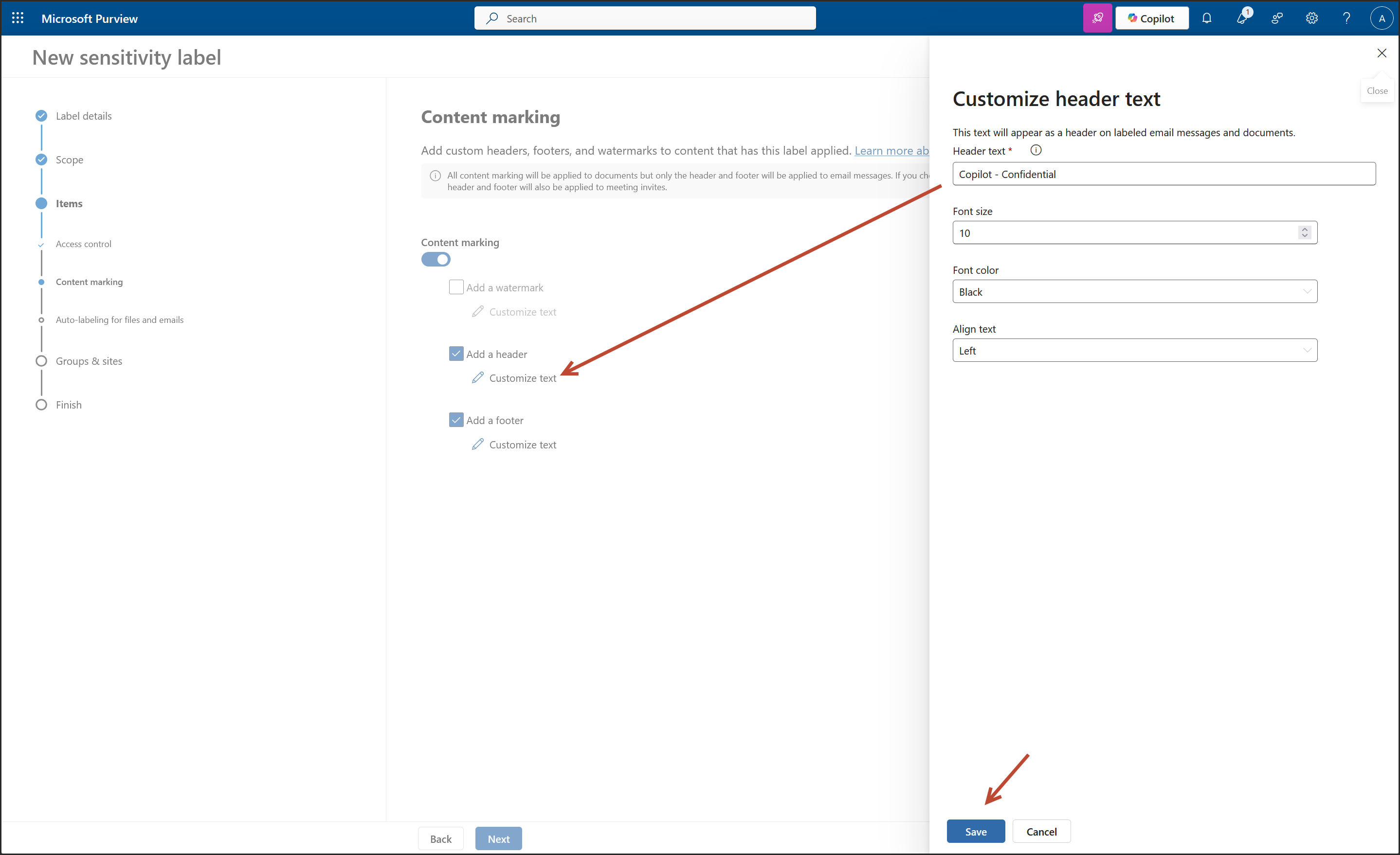
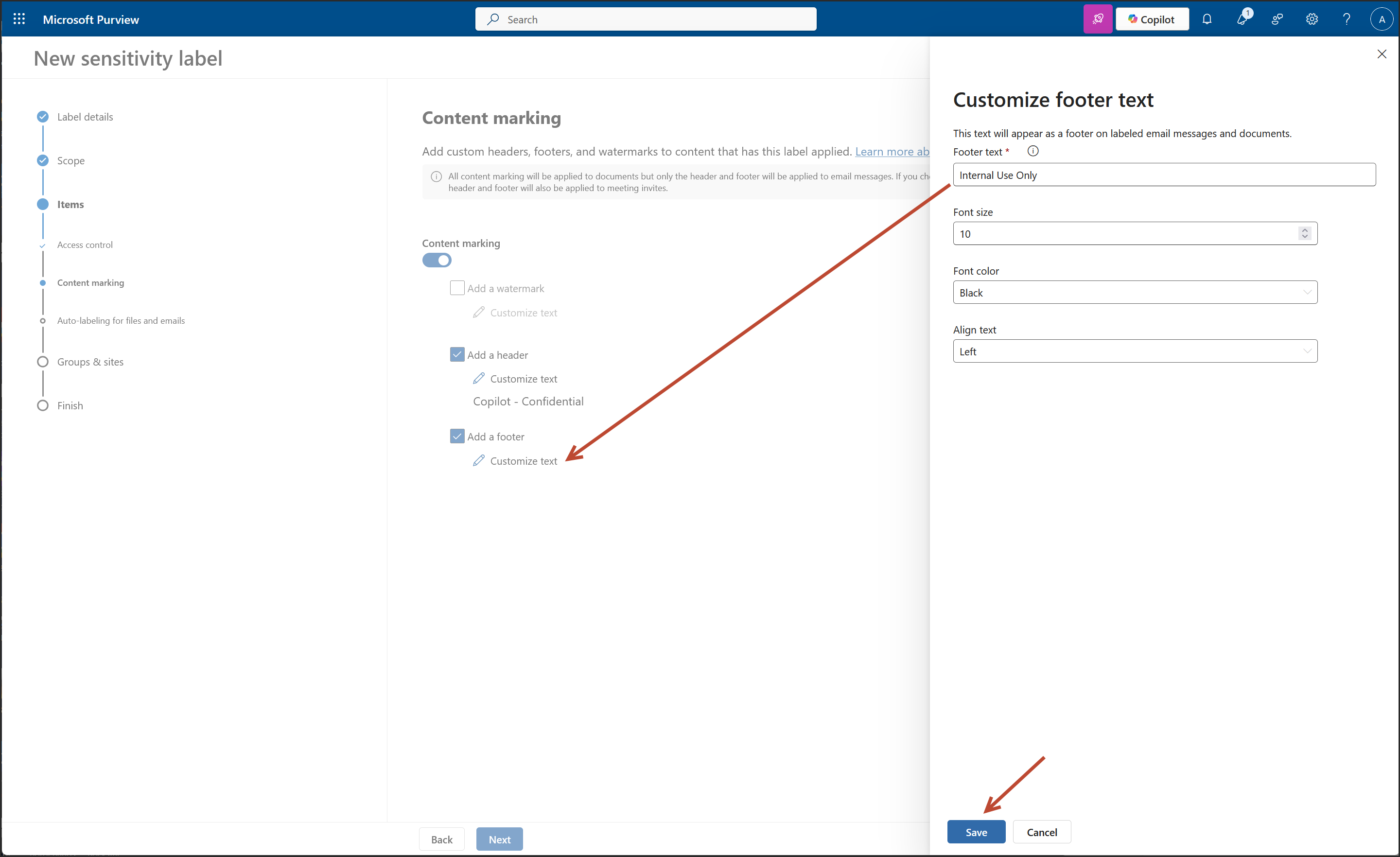
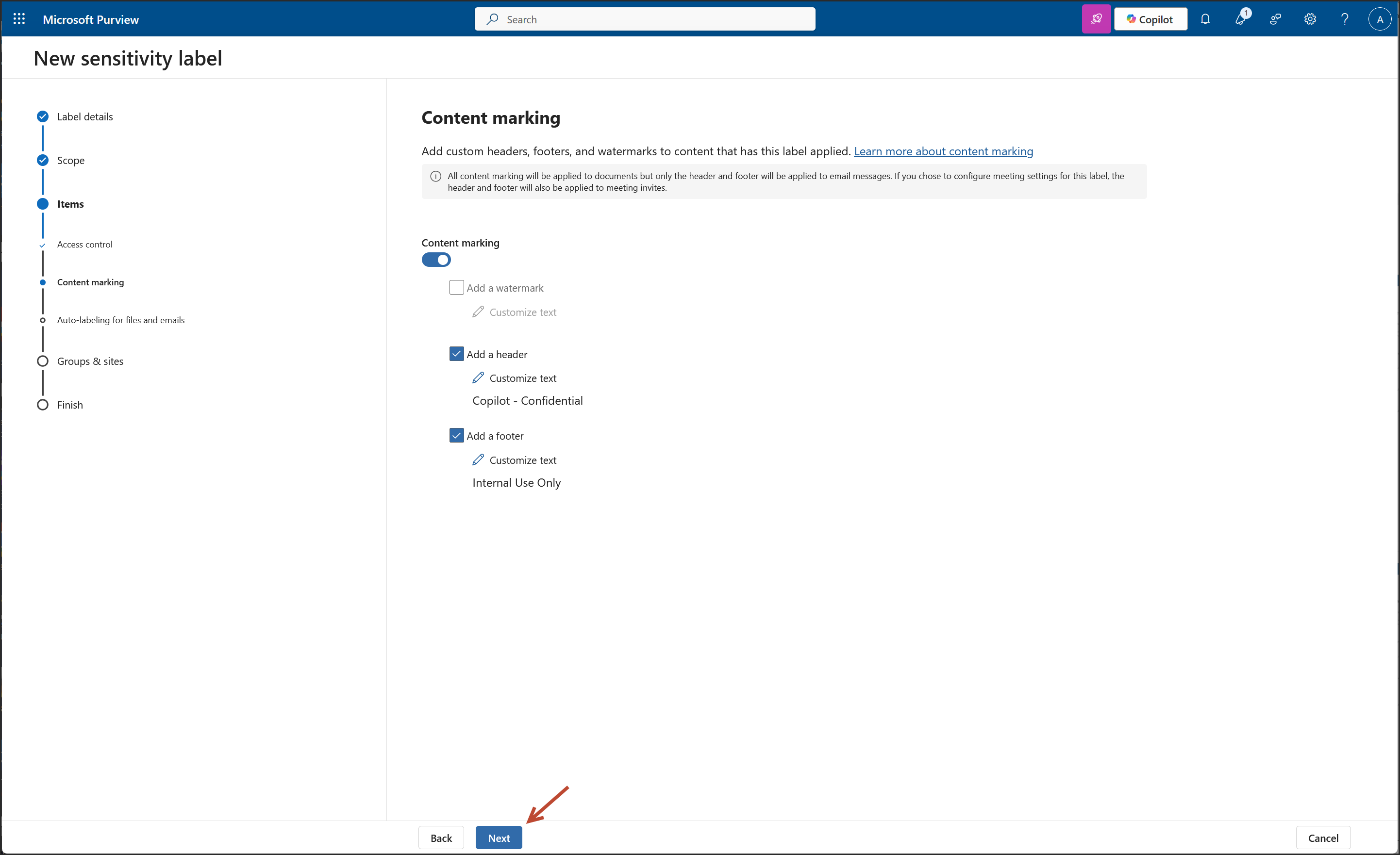
2. Create a New Sensitivity Label: "Copilot"
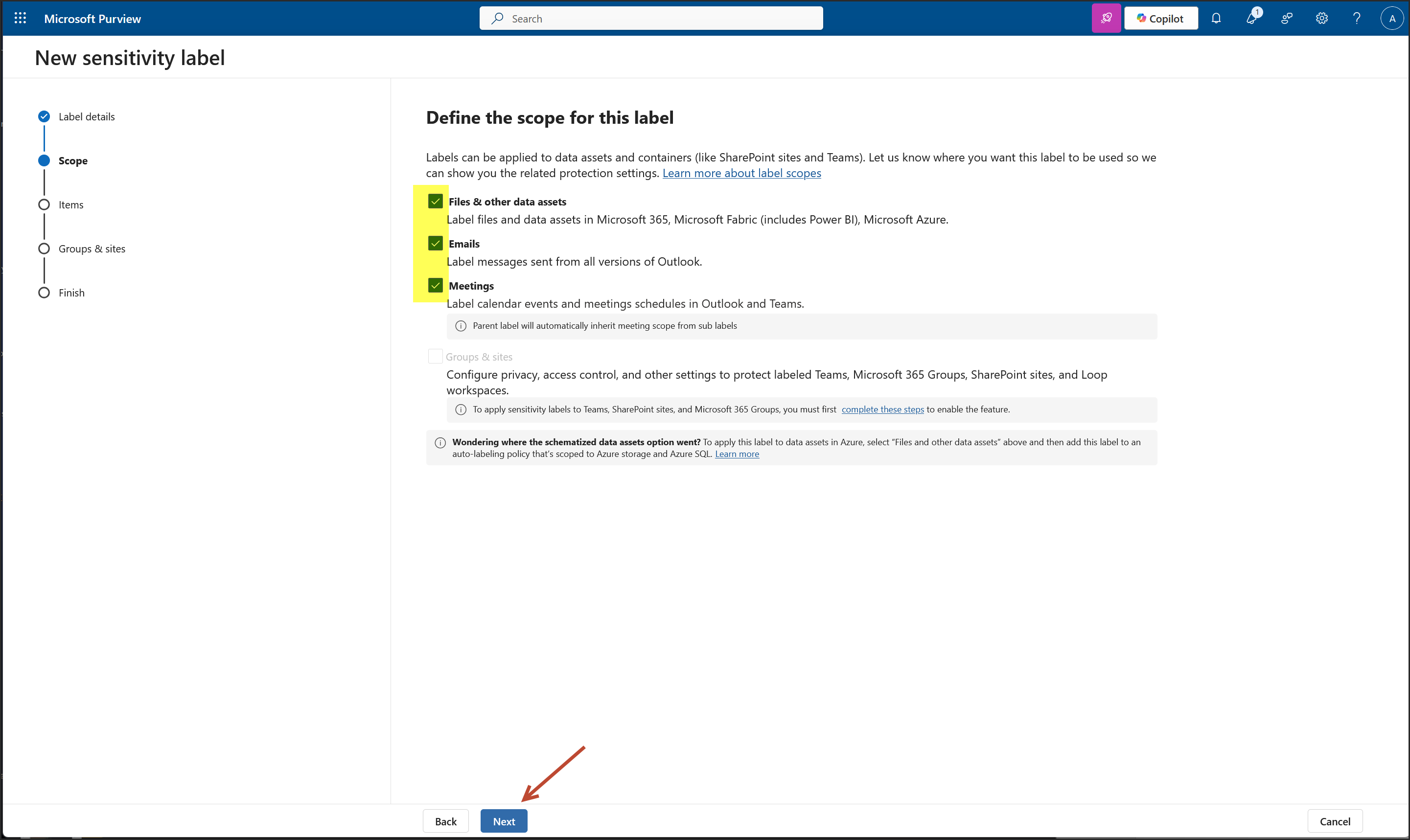
- Label Scope: Files, Emails, Meetings
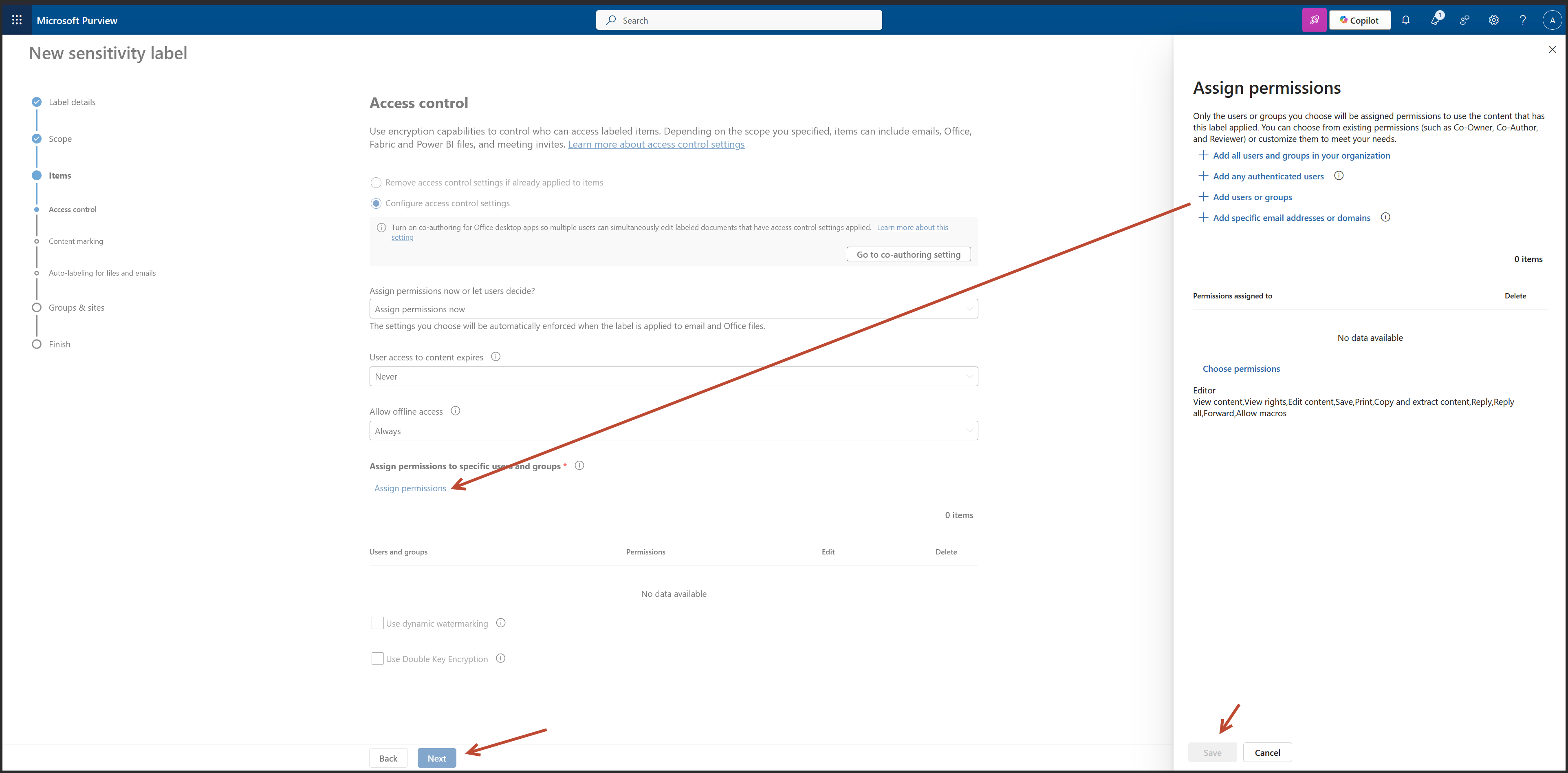
- Encryption: Enabled with assigned permissions
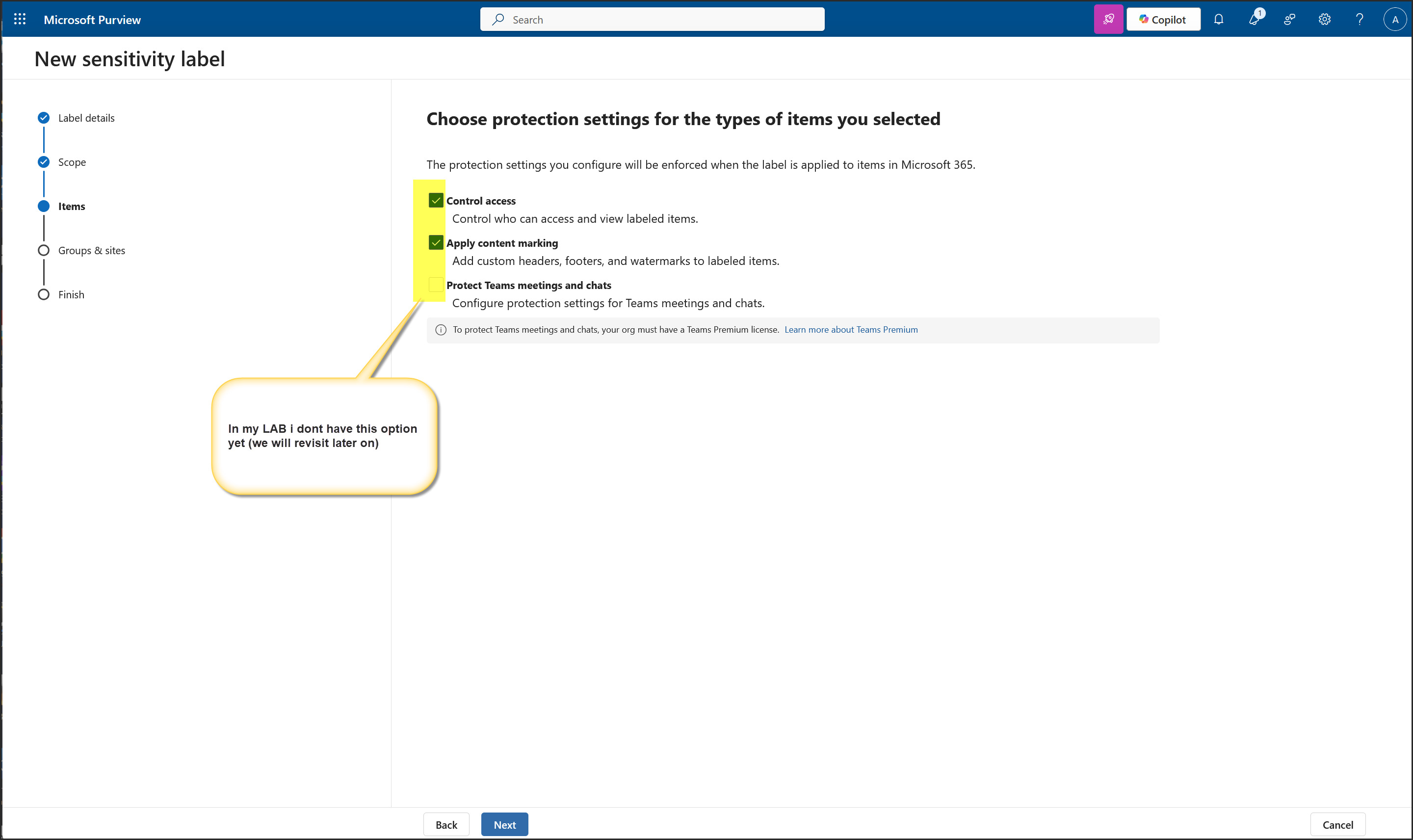
- Content Marking: Header, Footer, Watermark applied
- Teams Protection: Enabled (Teams Premium required)
- Auto-labeling: Optional toggle reviewed; policy not yet created
- Label Policy: Published to all users with mandatory labeling enforced
- Email Behavior: Inheritance from attachments enabled
- Purview Processing: Enabled for encrypted SharePoint/OneDrive content
Go to Purview Information Protection
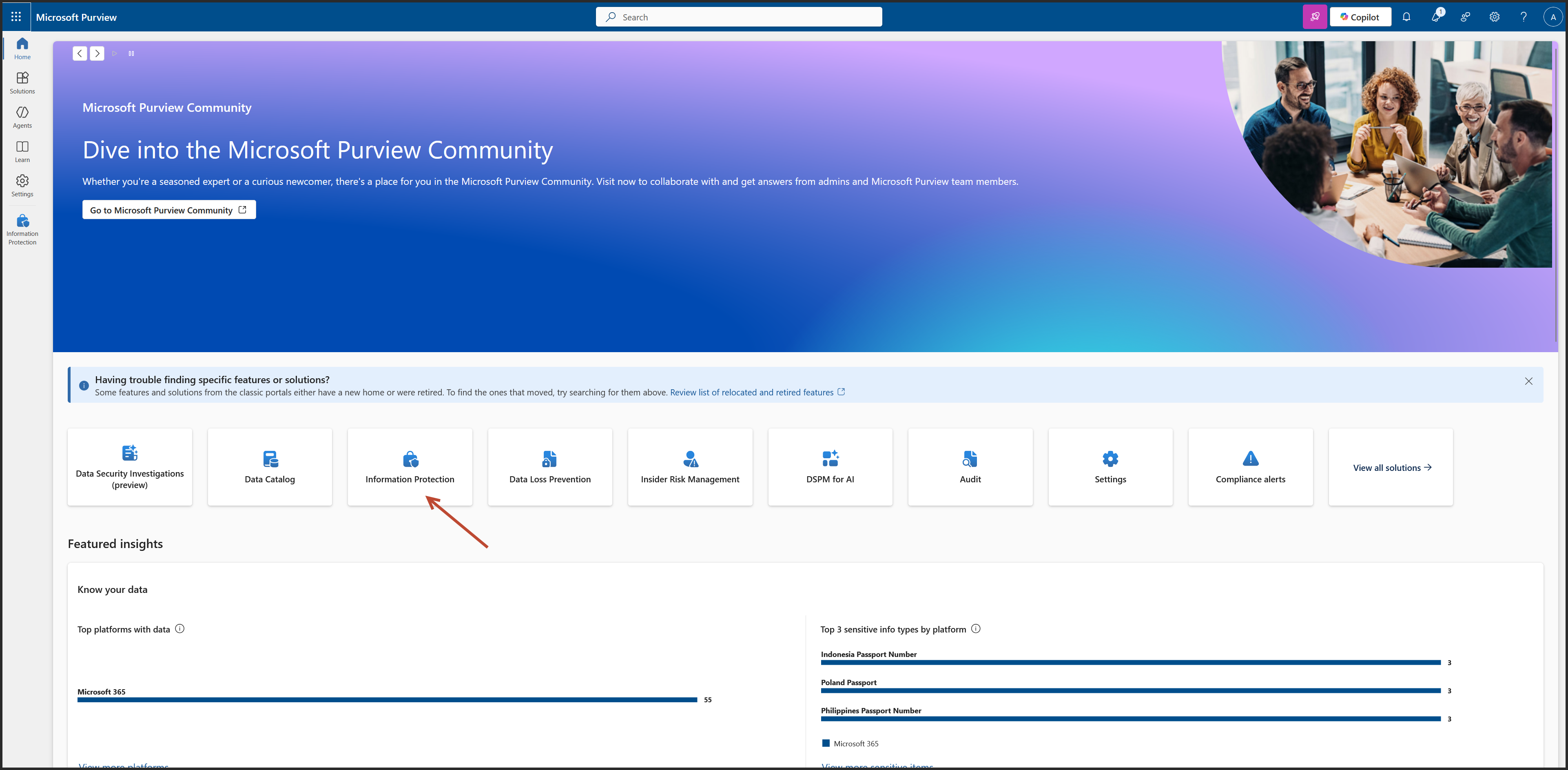
Sensitivity labels > Create a label
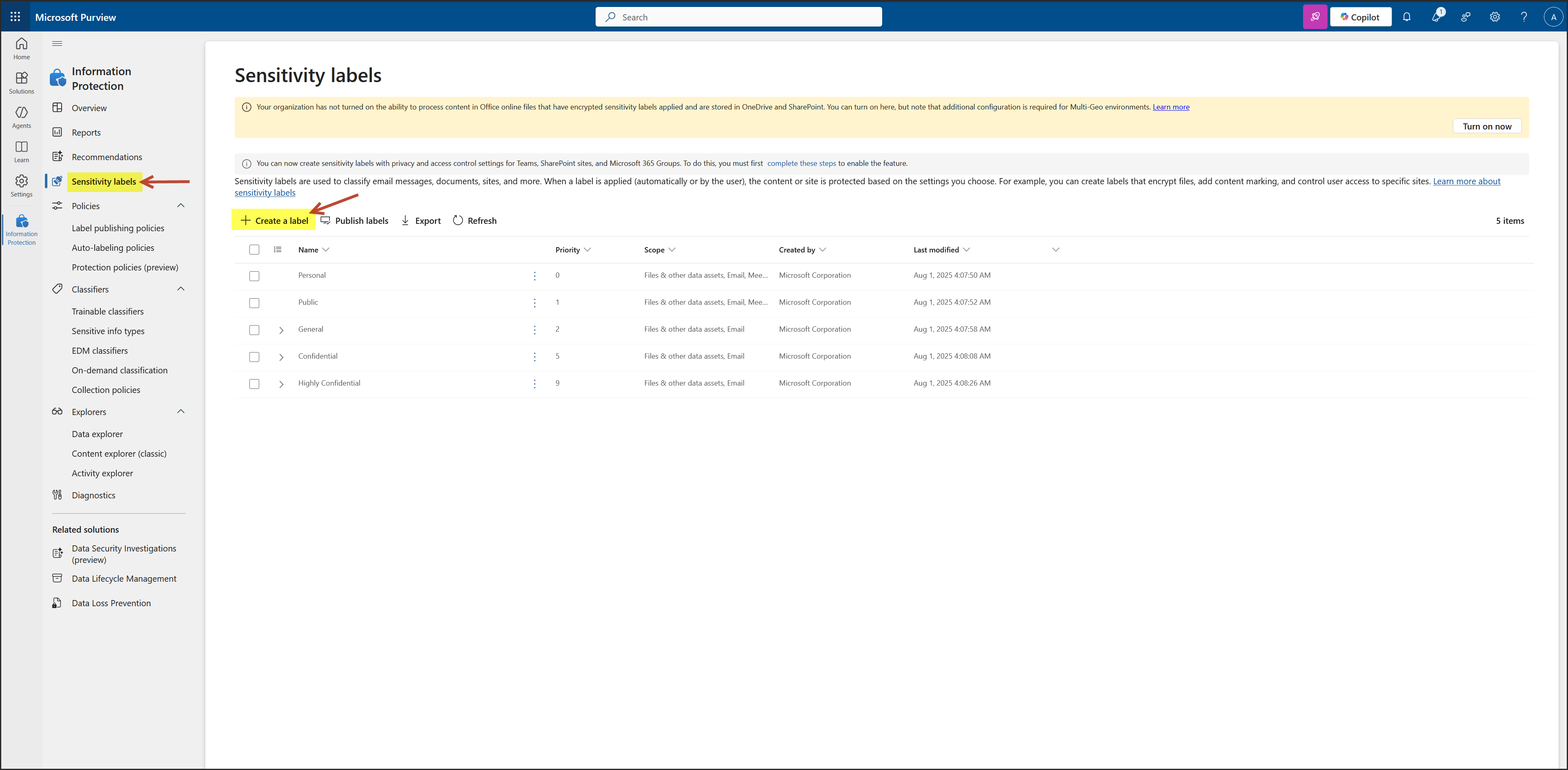
 Here add the Entra Group
Here add the Entra Group
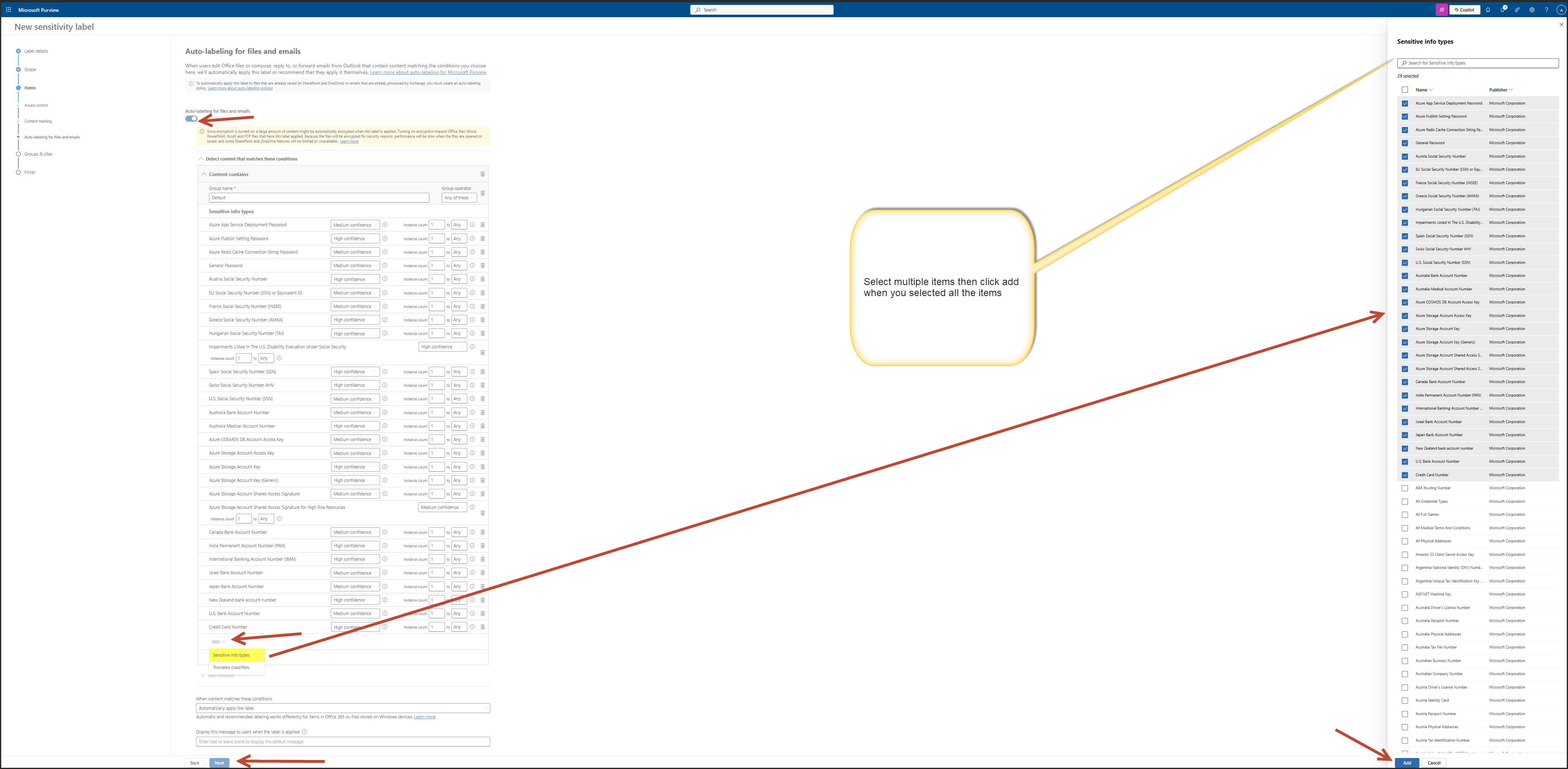
Searched Sensitive Info Types
I searched for the following types of sensitive information:
- Social Security numbers
- Credit card numbers
- Account numbers
- General account identifiers
- ABA routing numbers
- Any other data you wouldn’t want exposed
Here is the link: More information about the dependencies for the unmanaged devices option

Copilot sensitivity label was successfully created
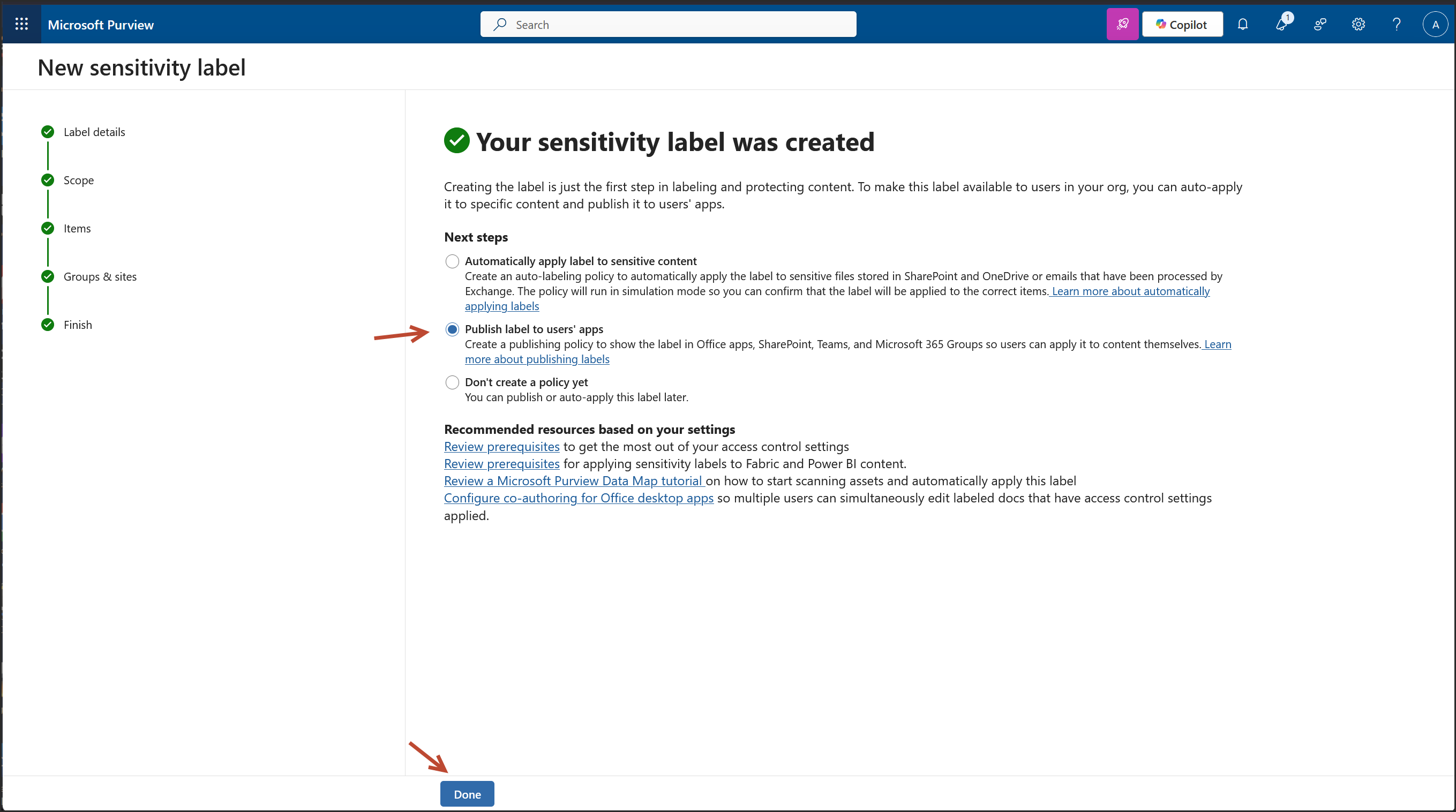 Next Steps (from the confirmation screen)
Next Steps (from the confirmation screen)
Publish the Label – Click DONE
Links from This Screen
- Apply Sensitivity Label Automatically: Microsoft Learn – Apply Sensitivity Label Automatically
- Publish Sensitivity Labels by Creating a Label Policy: Microsoft Learn – Publish Sensitivity Labels via Label Policy
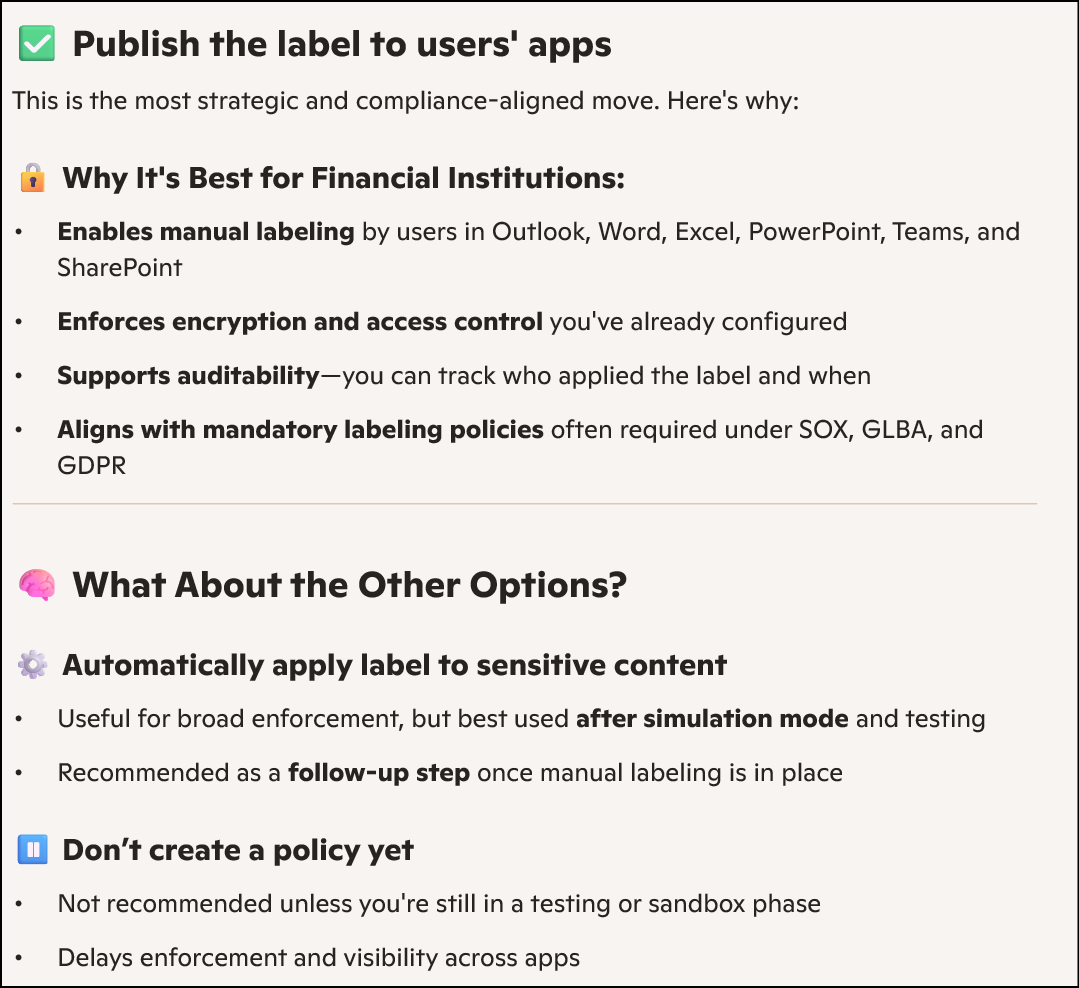
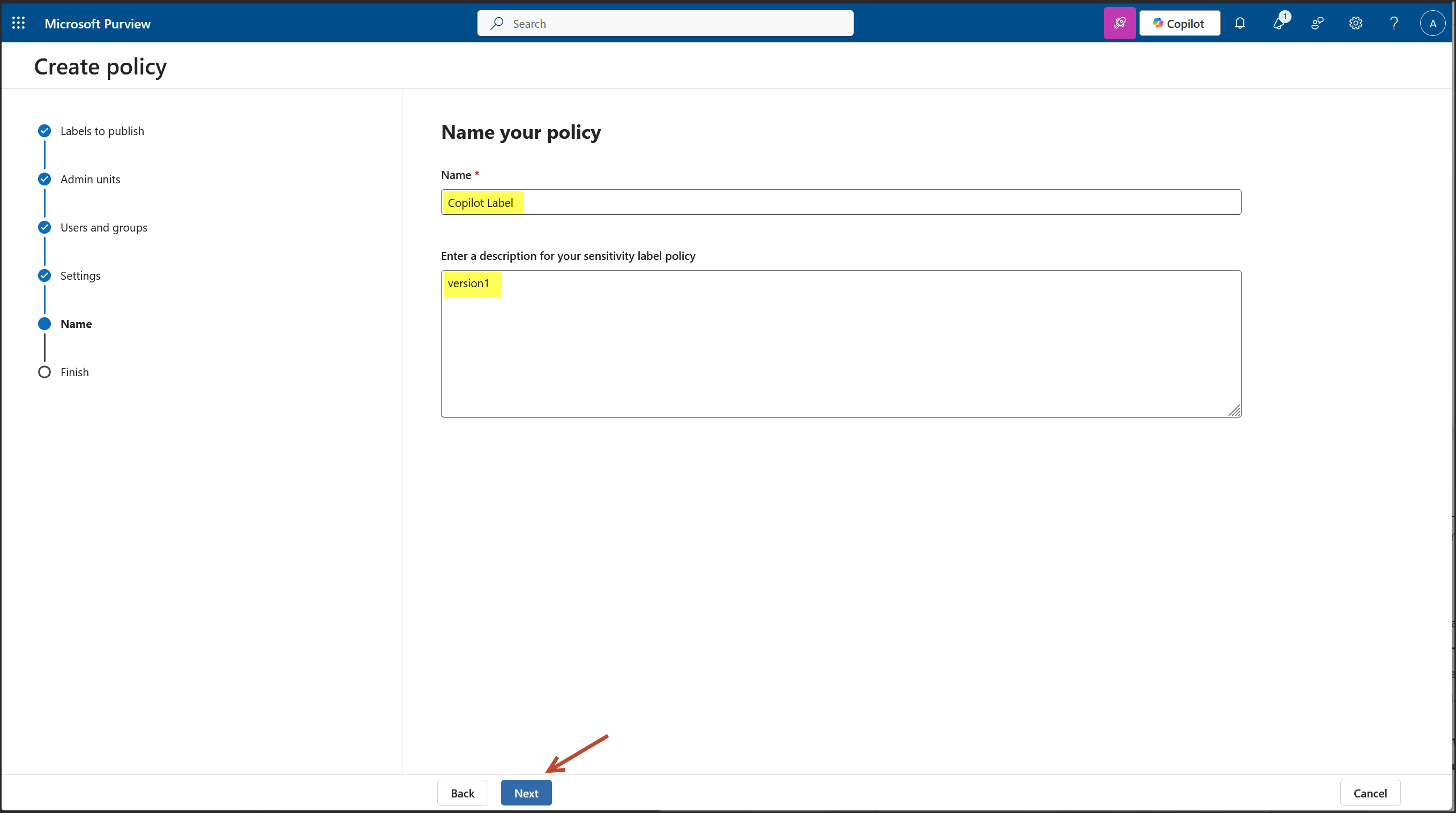
Why I Selected “Publish Label to Users’ App”
Publishing the label ensures visibility and enforcement across supported applications, enabling consistent protection and user-driven classification. This step is essential for operationalizing the label within the user experience.
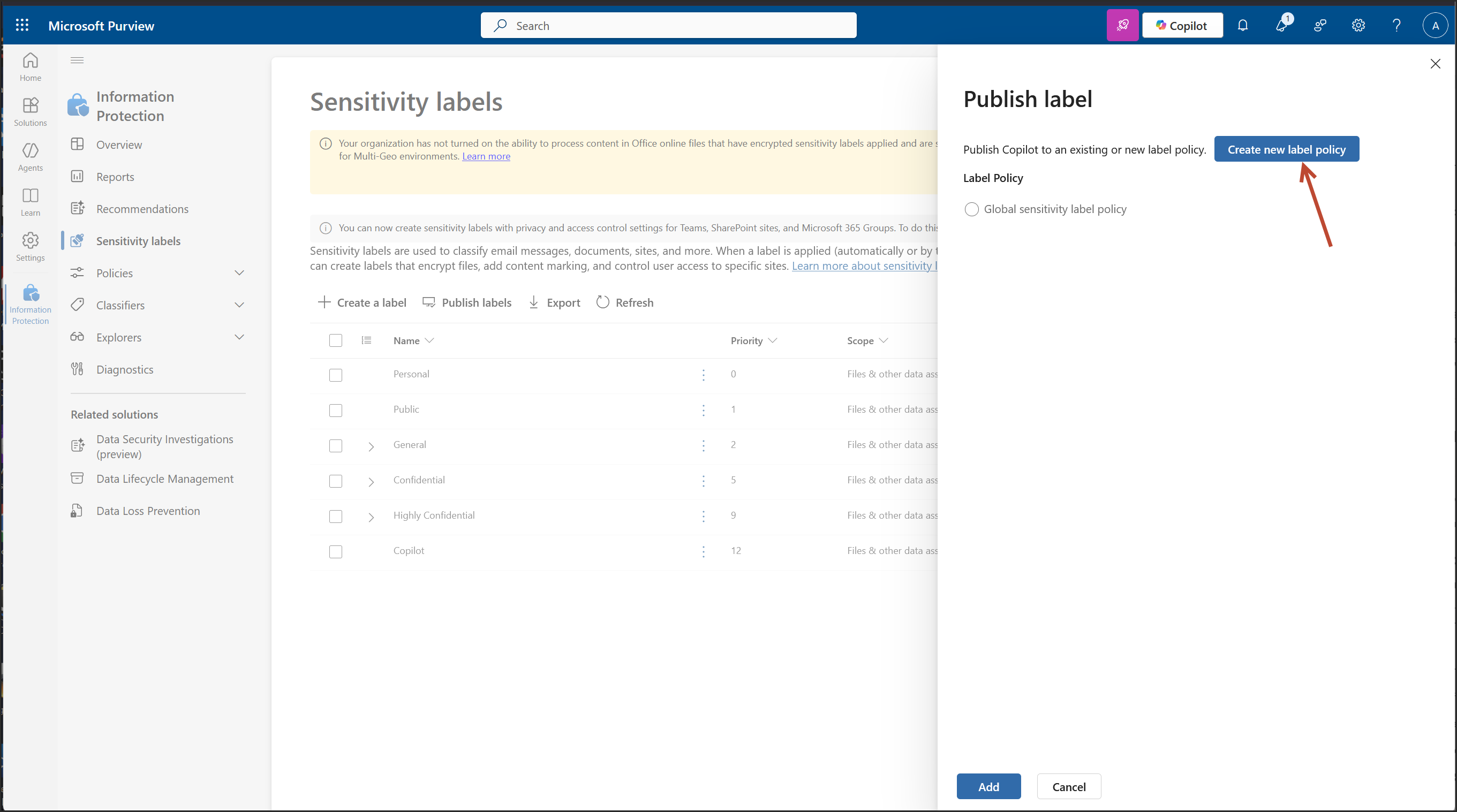
This screen confirms your Copilot sensitivity label is created, and now you're in the publishing workflow. This is where you make the label available to users and services across Microsoft 365.
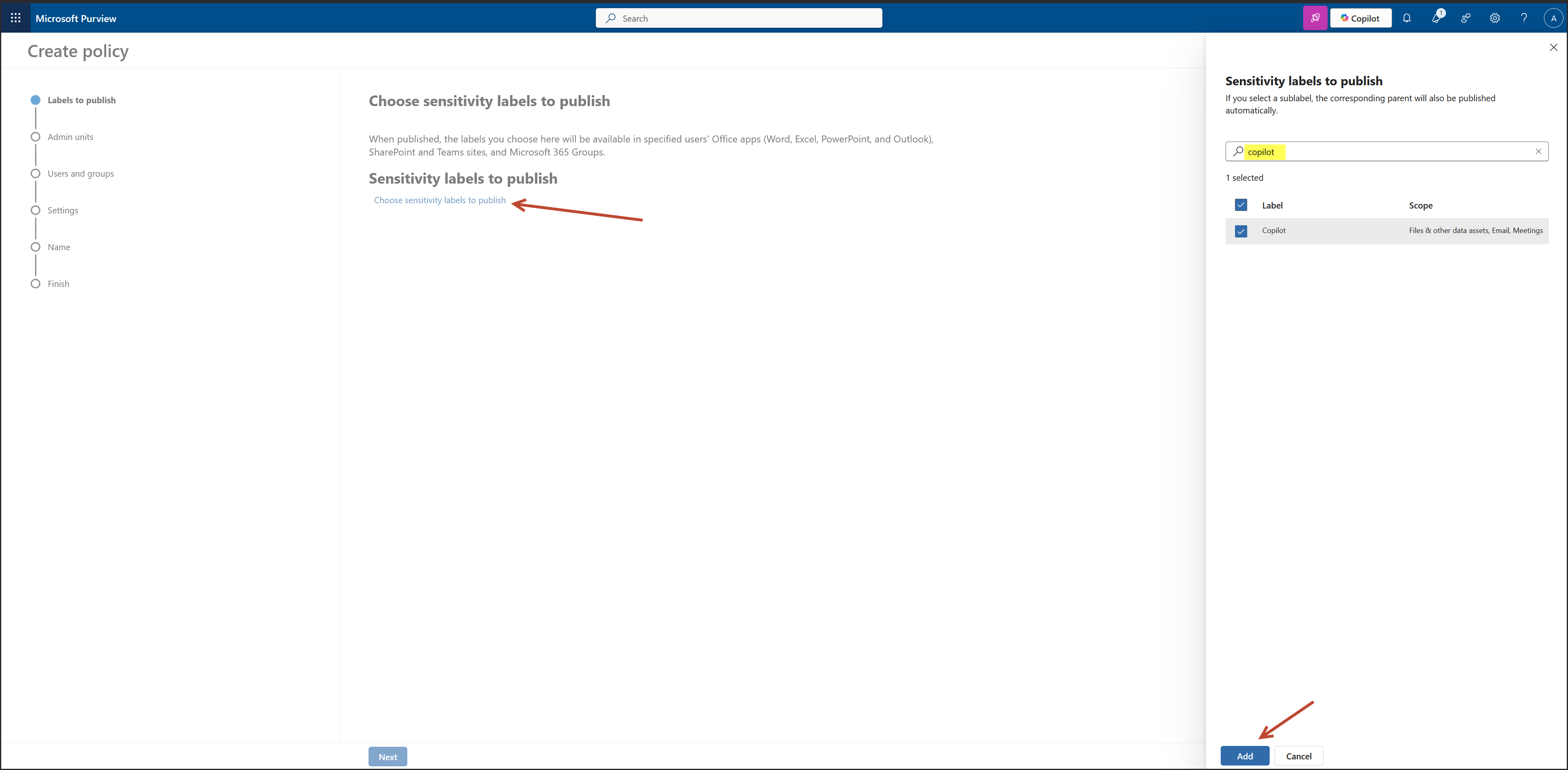
This is the “Choose sensitivity labels to publish” step in the label policy wizard.
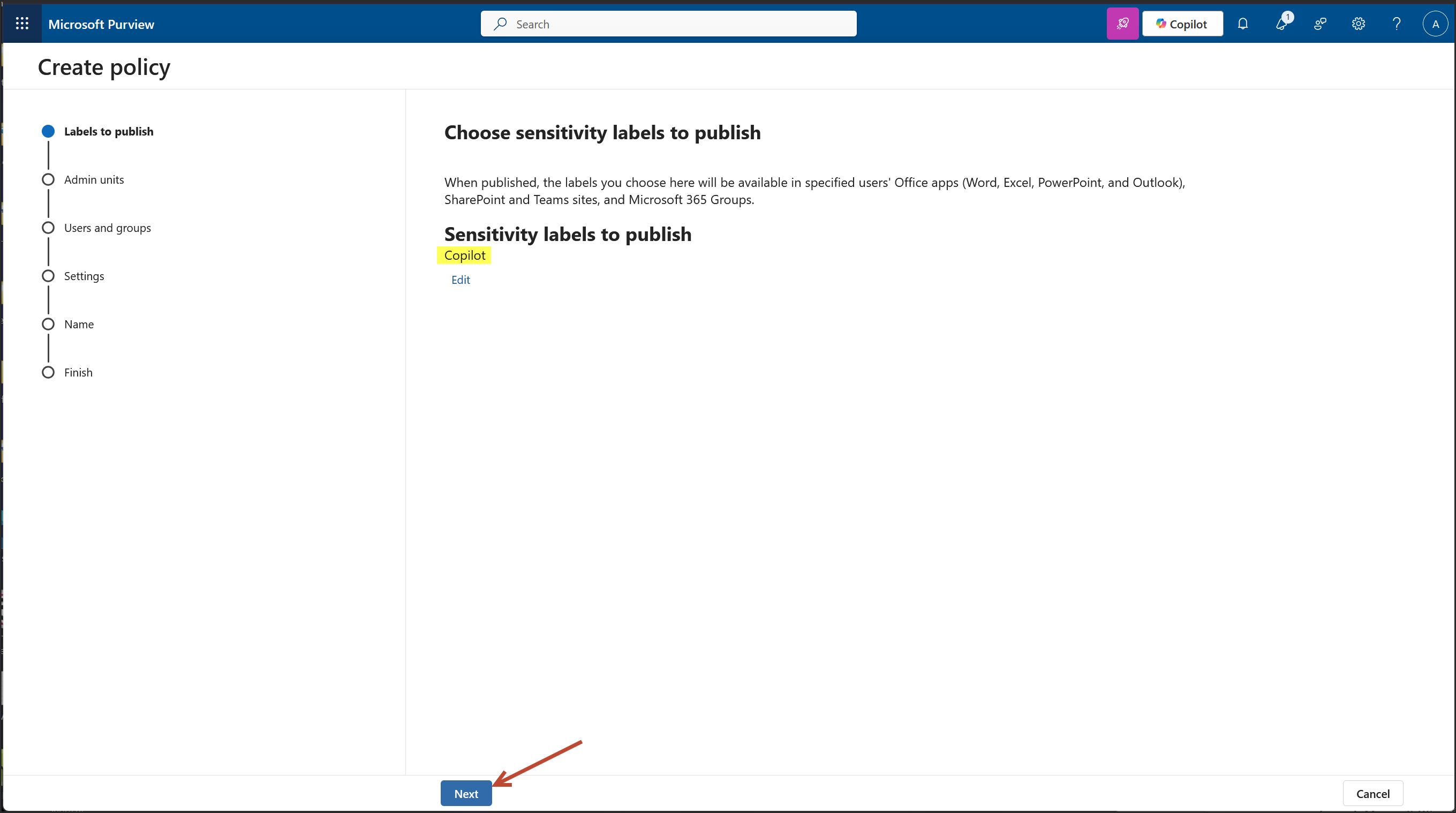
Here's what to do next to lock in your Copilot label for enterprise use:
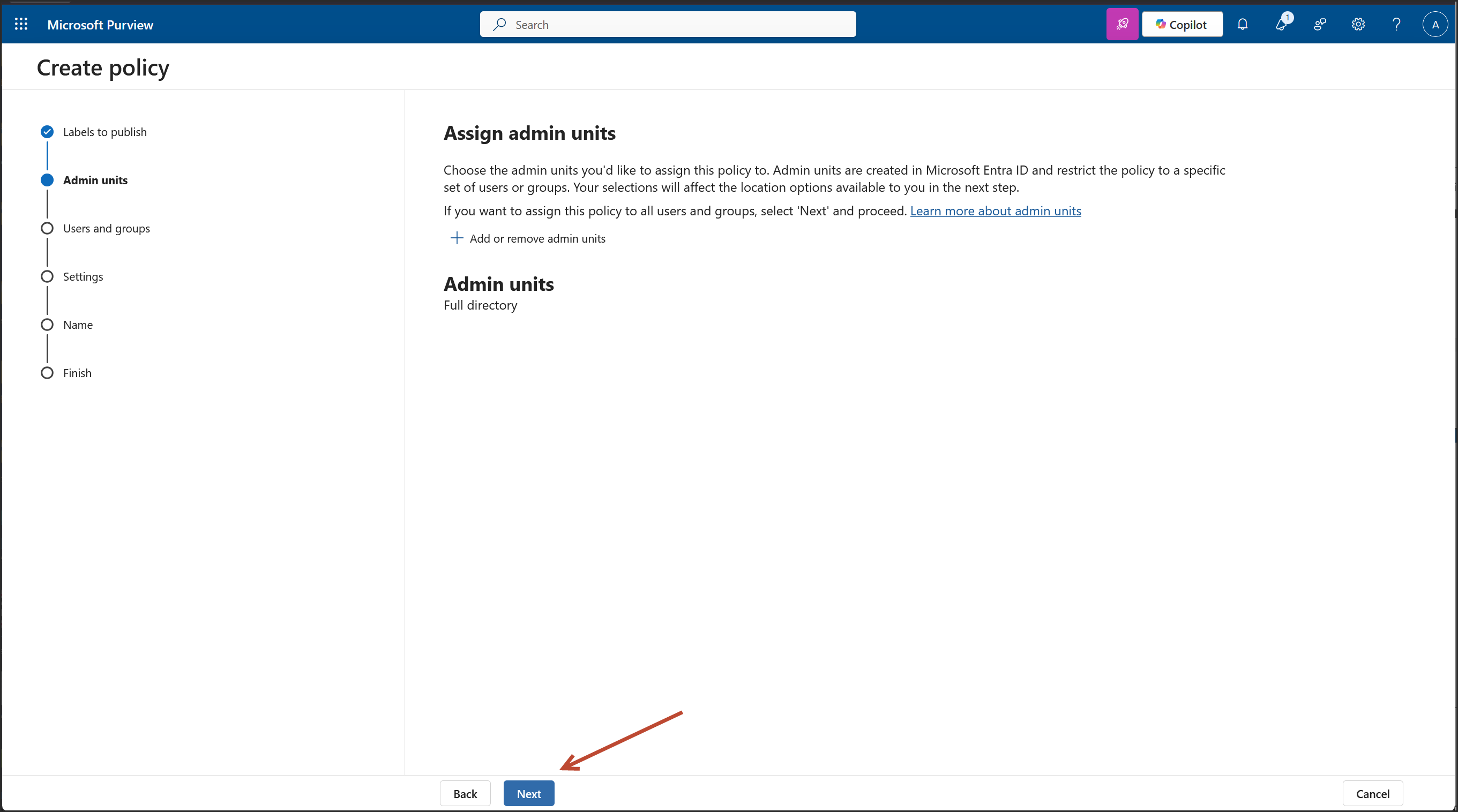 Link: https://learn.microsoft.com/en-us/purview/purview-admin-units
Link: https://learn.microsoft.com/en-us/purview/purview-admin-units
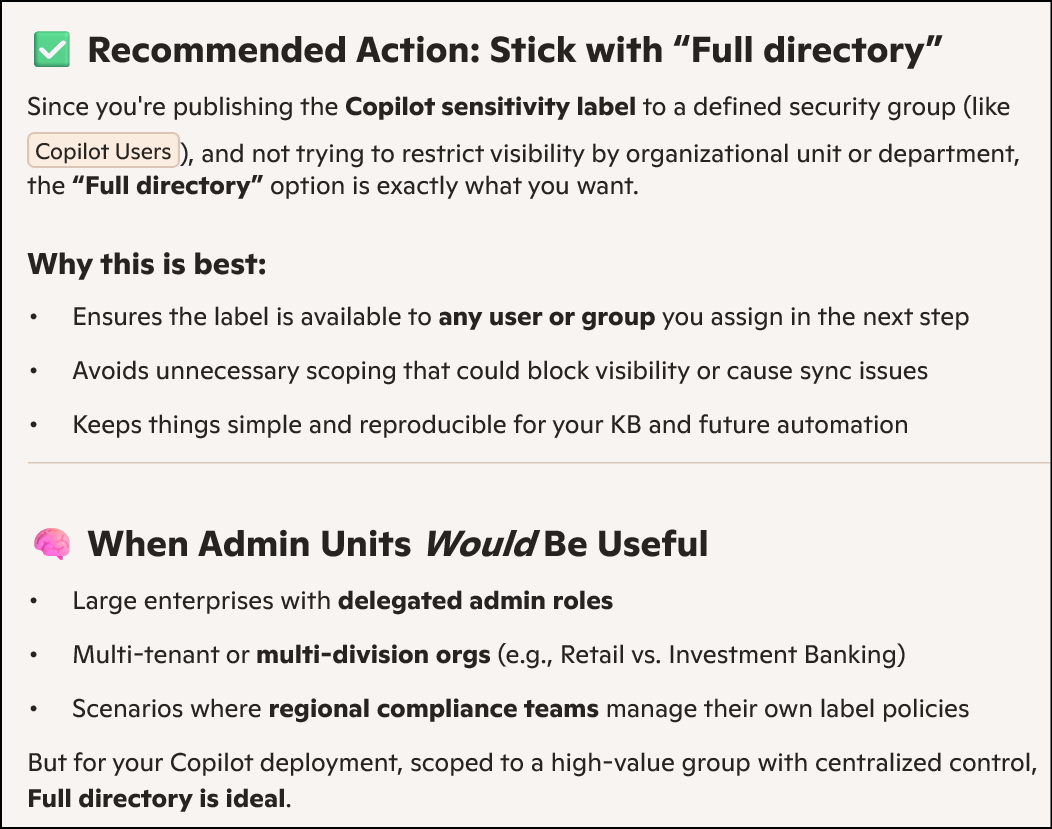
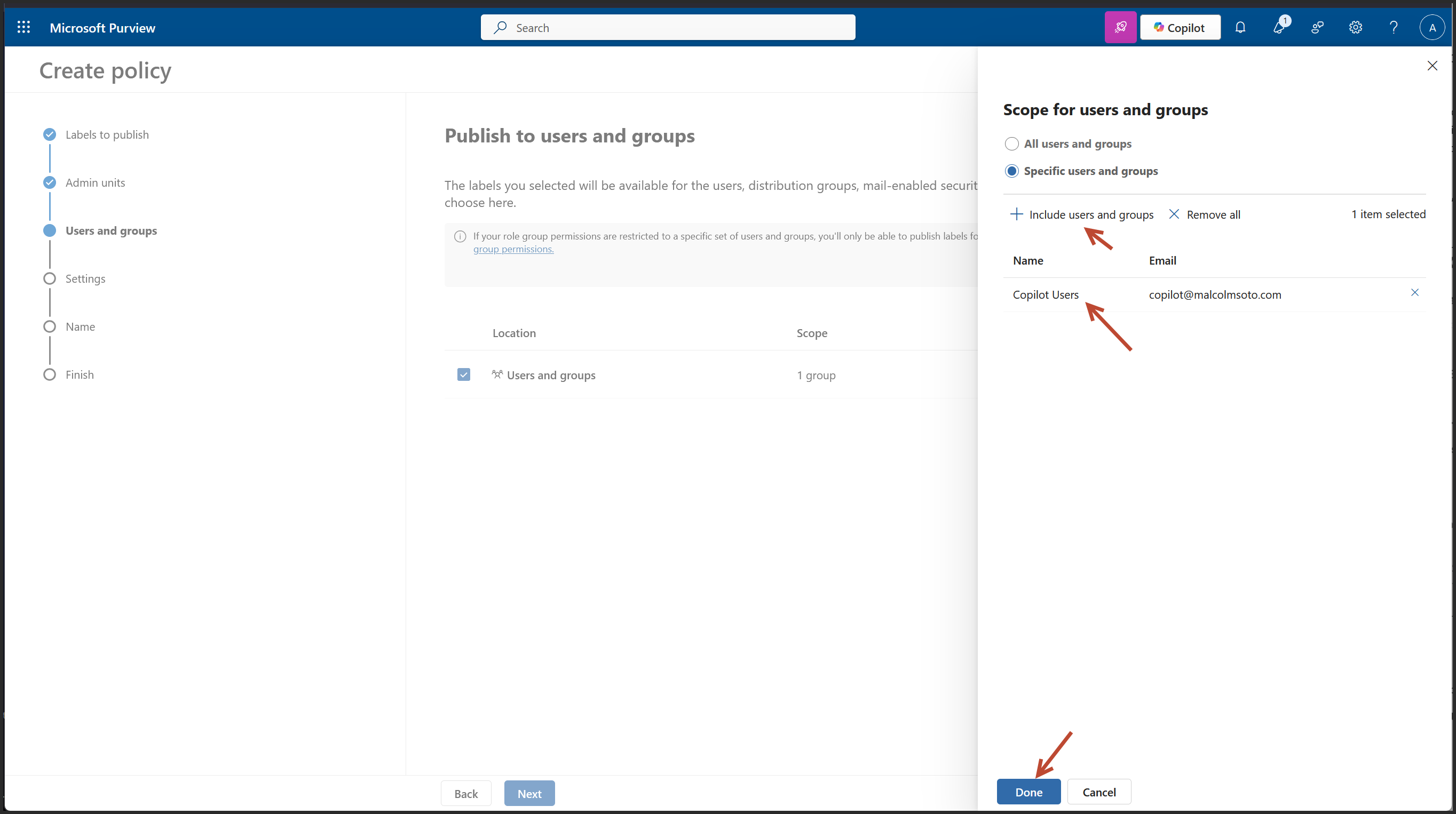
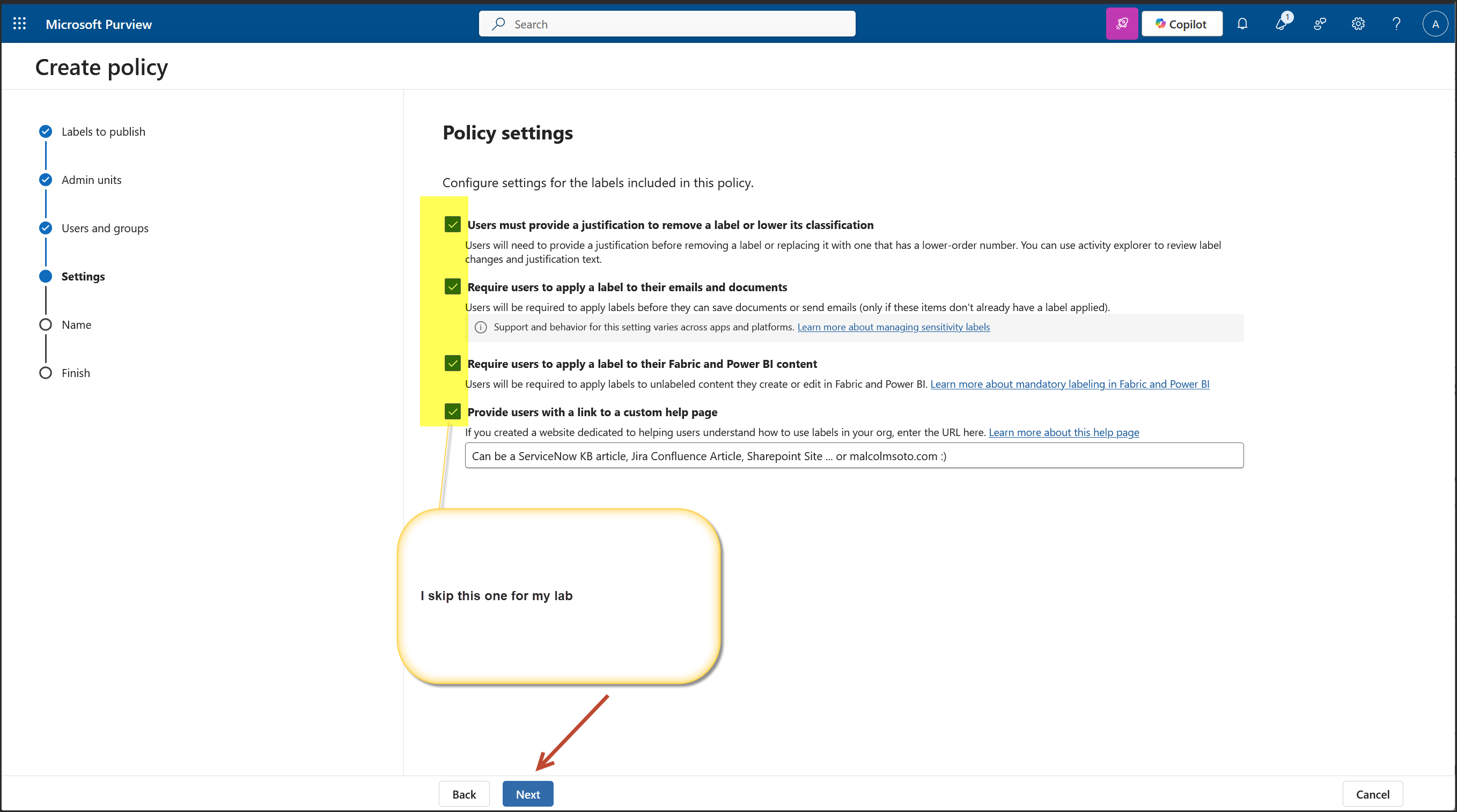
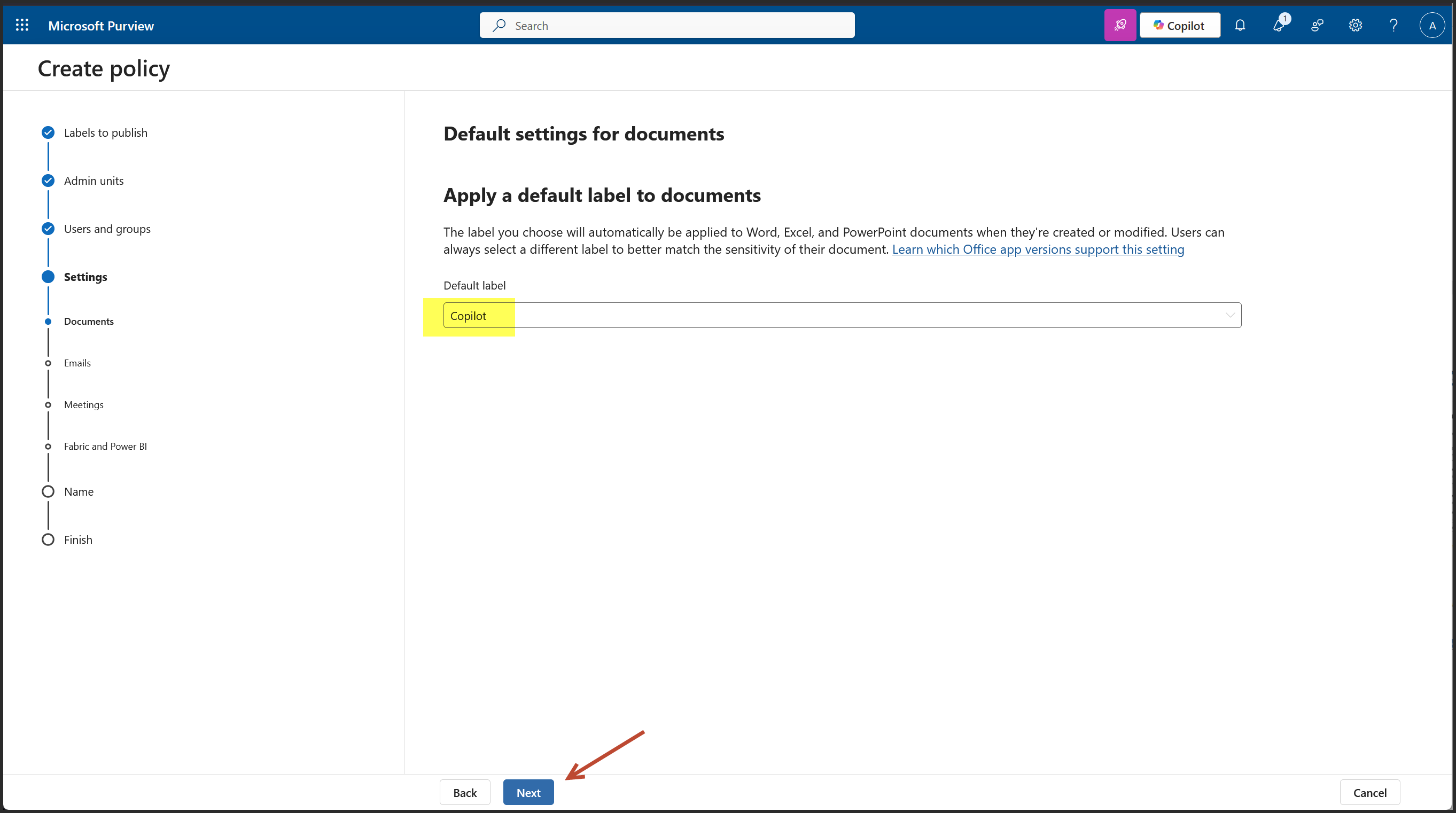
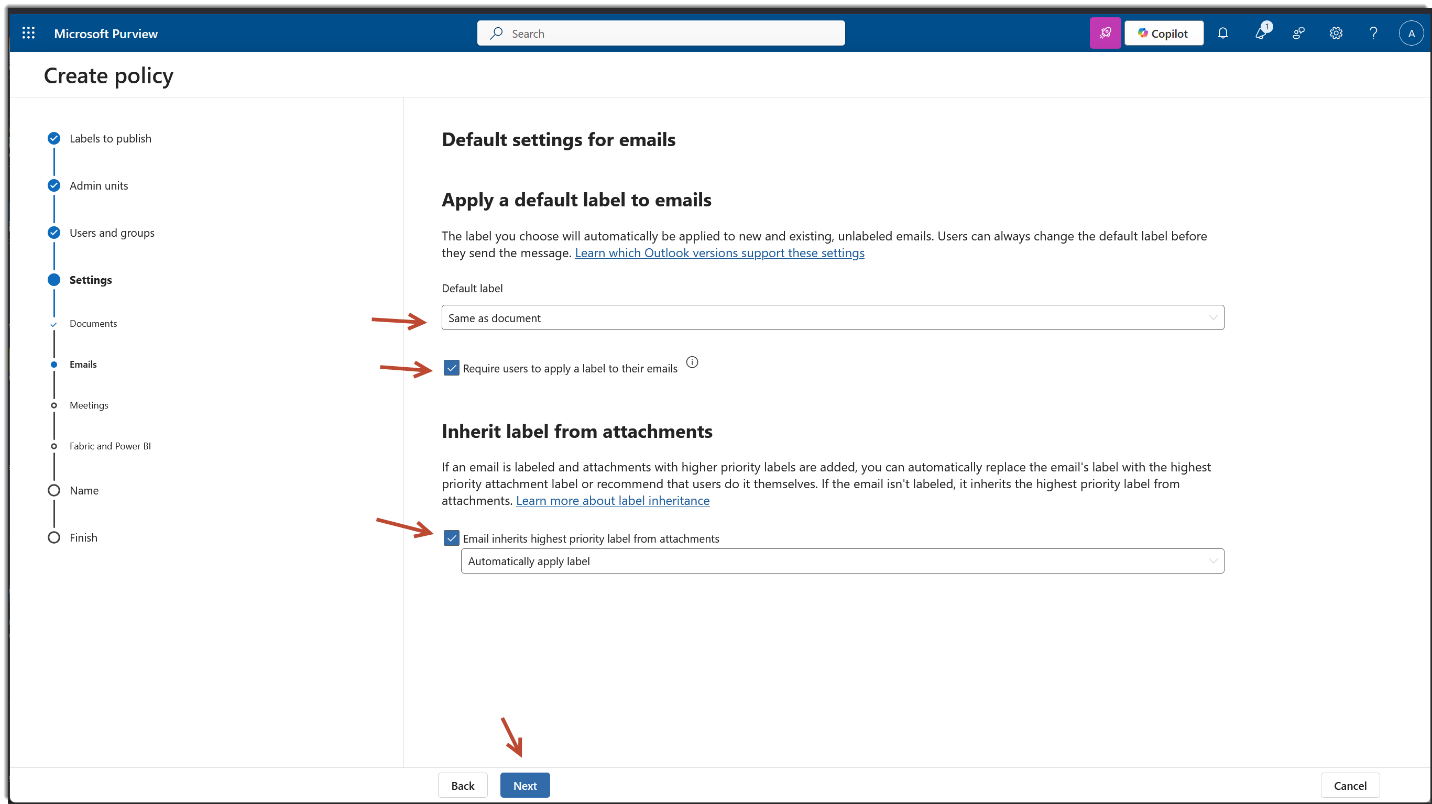
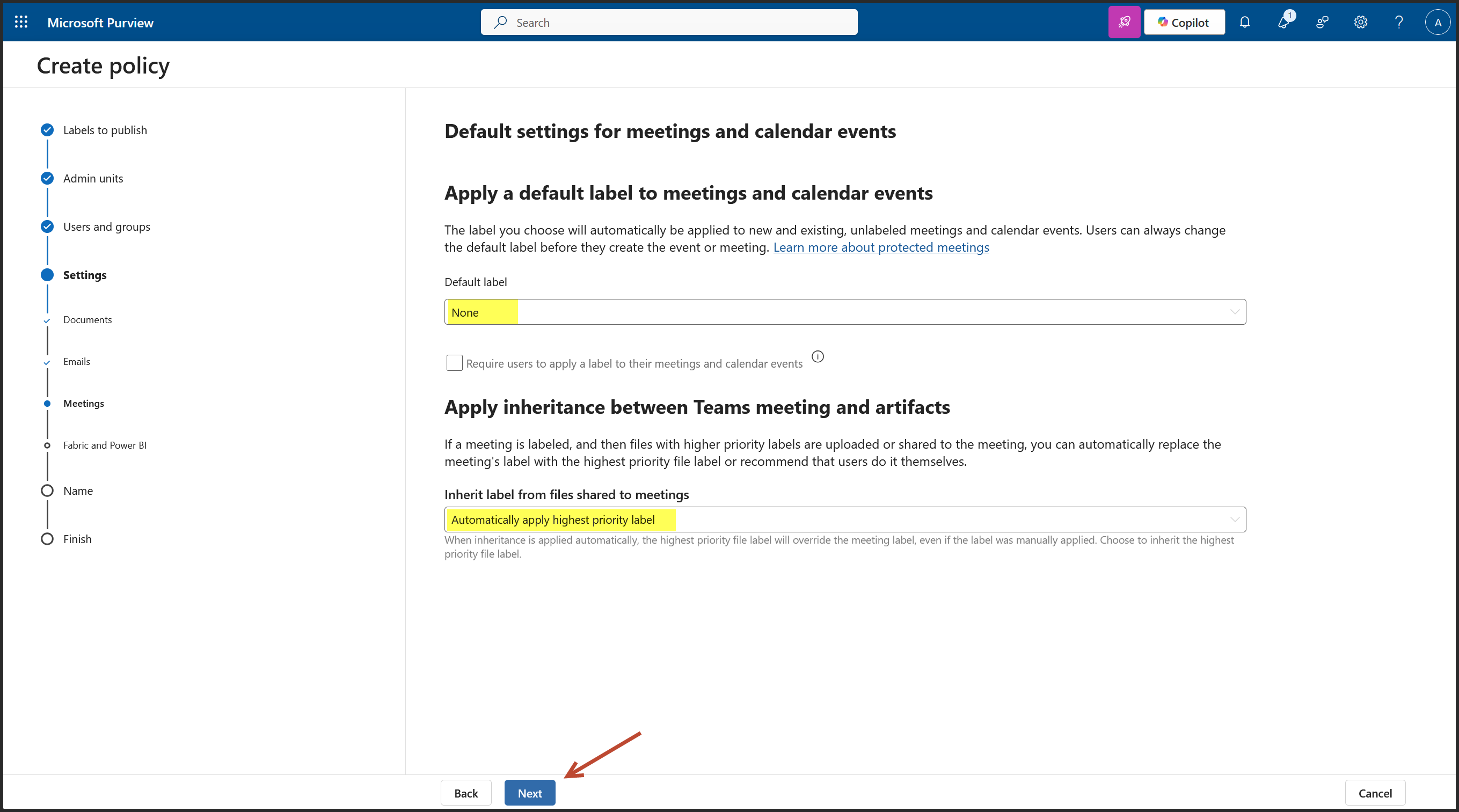
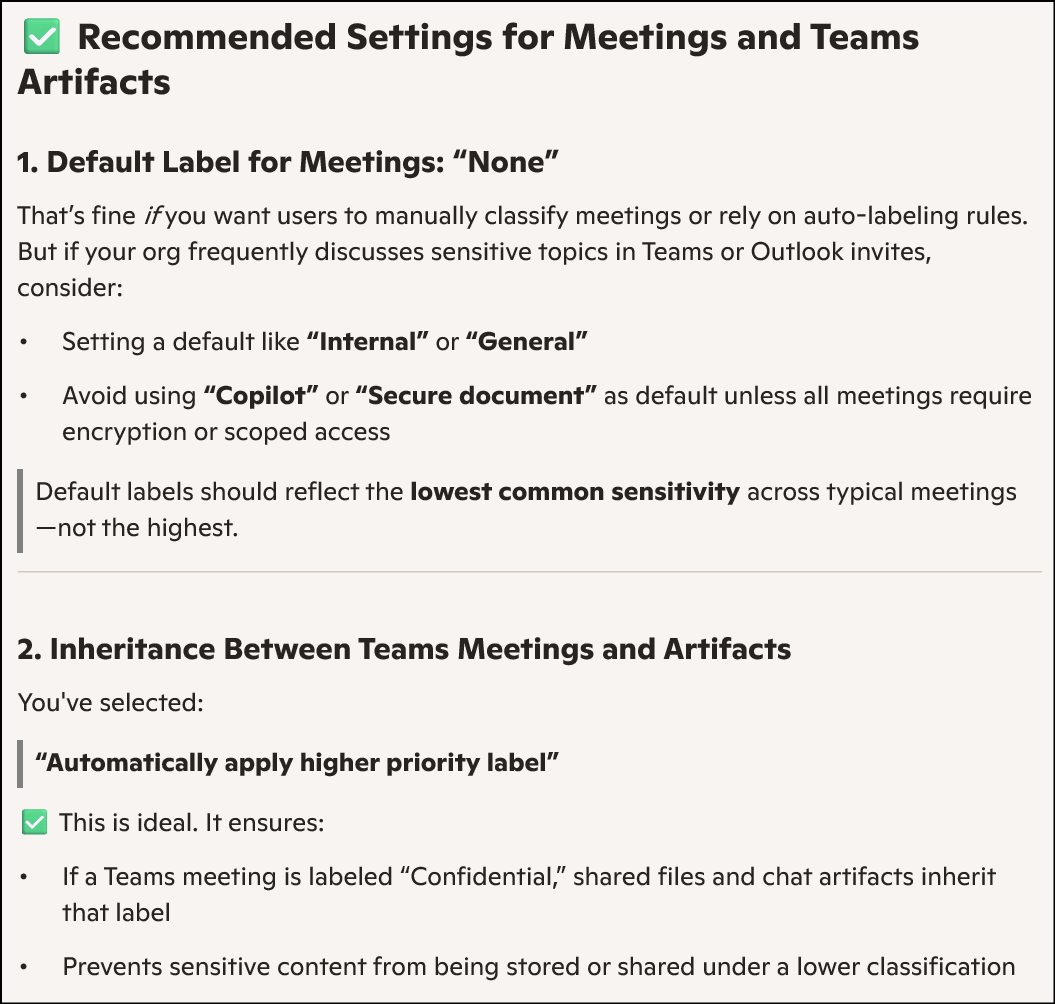
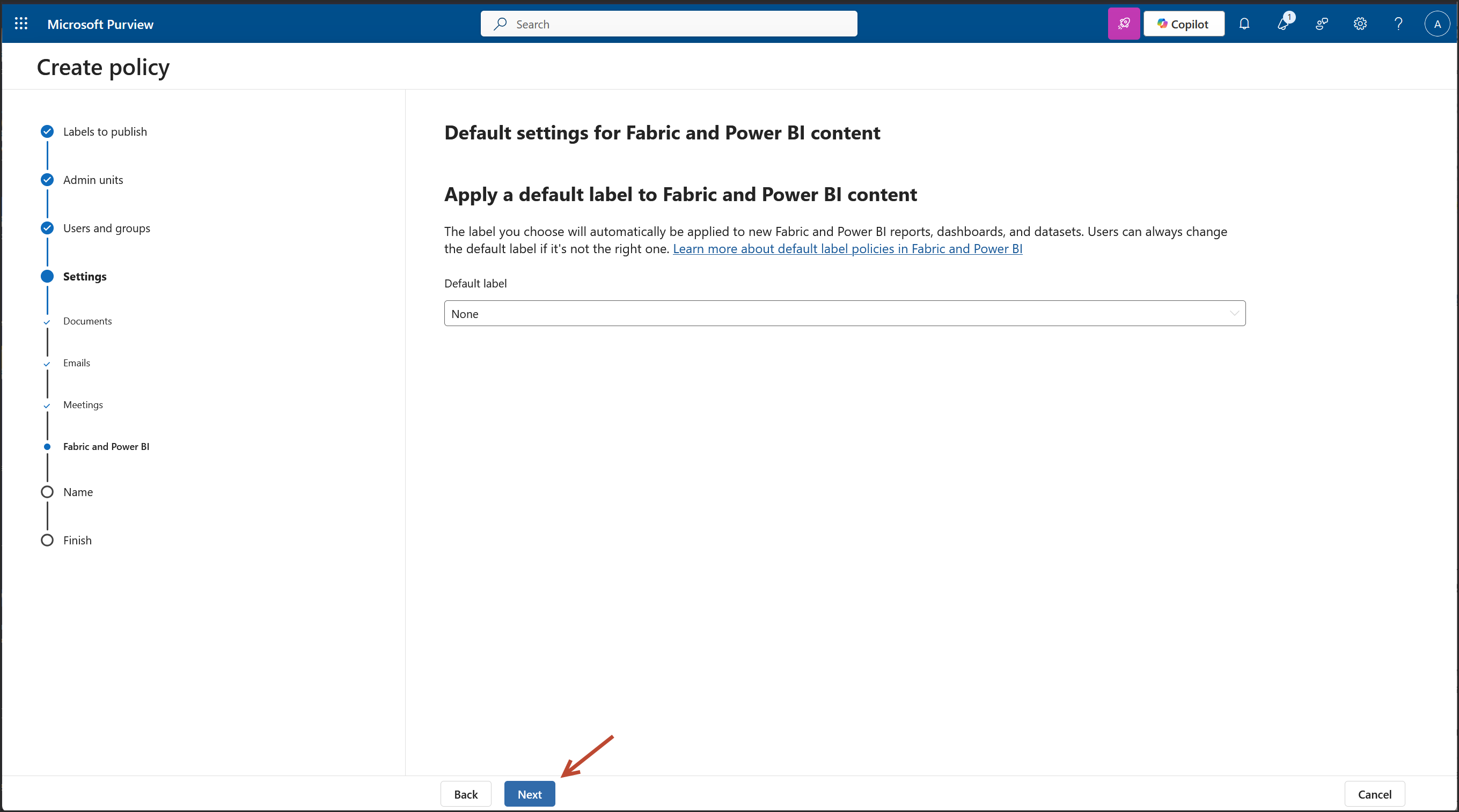
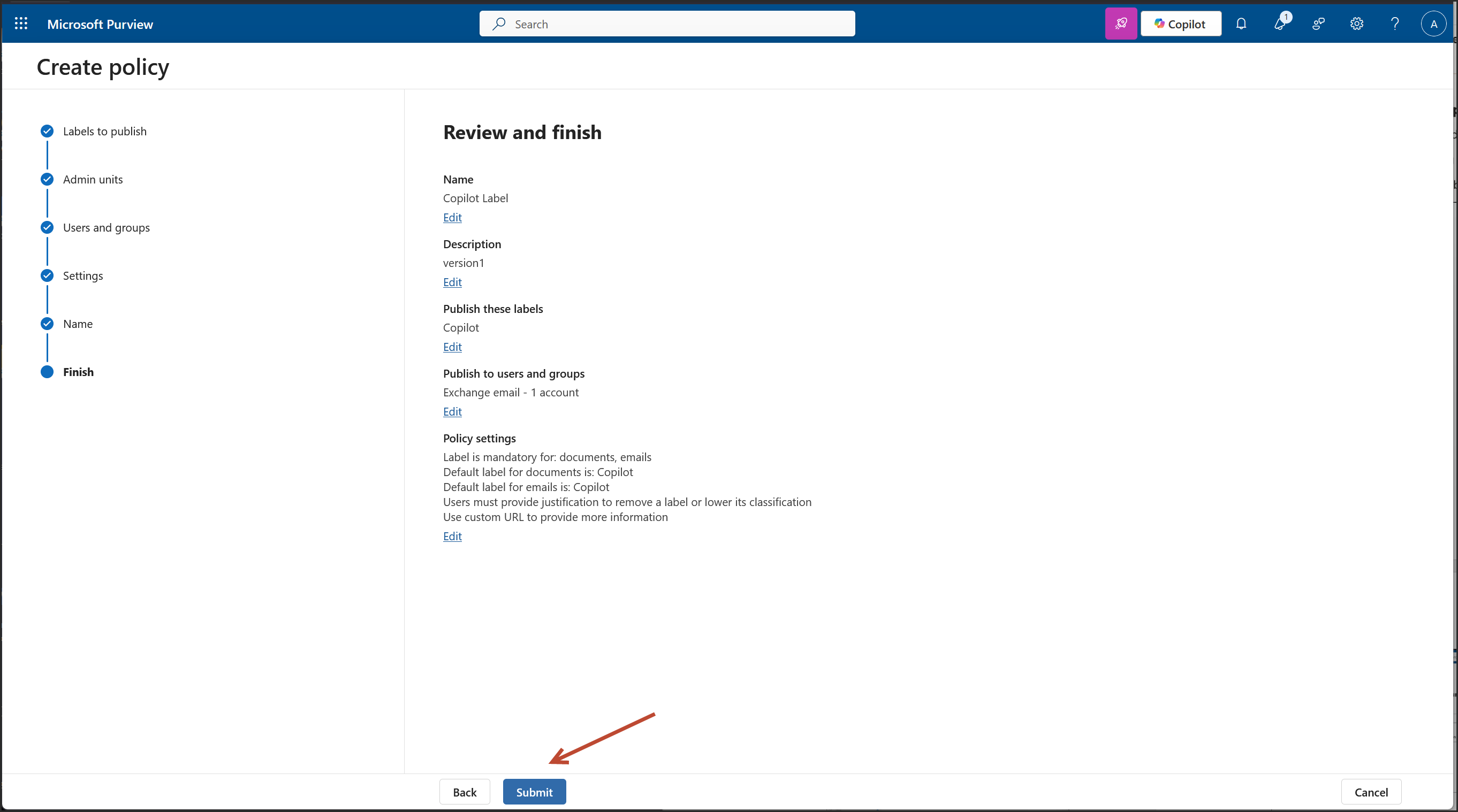
We are on the Policy Settings step of the label publishing wizard. This is where you define how strict or user friendly the Copilot label enforcement should be across apps like Outlook, Word, Excel, PowerPoint, and Power BI.
For a financial grade deployment, here's what’s best:

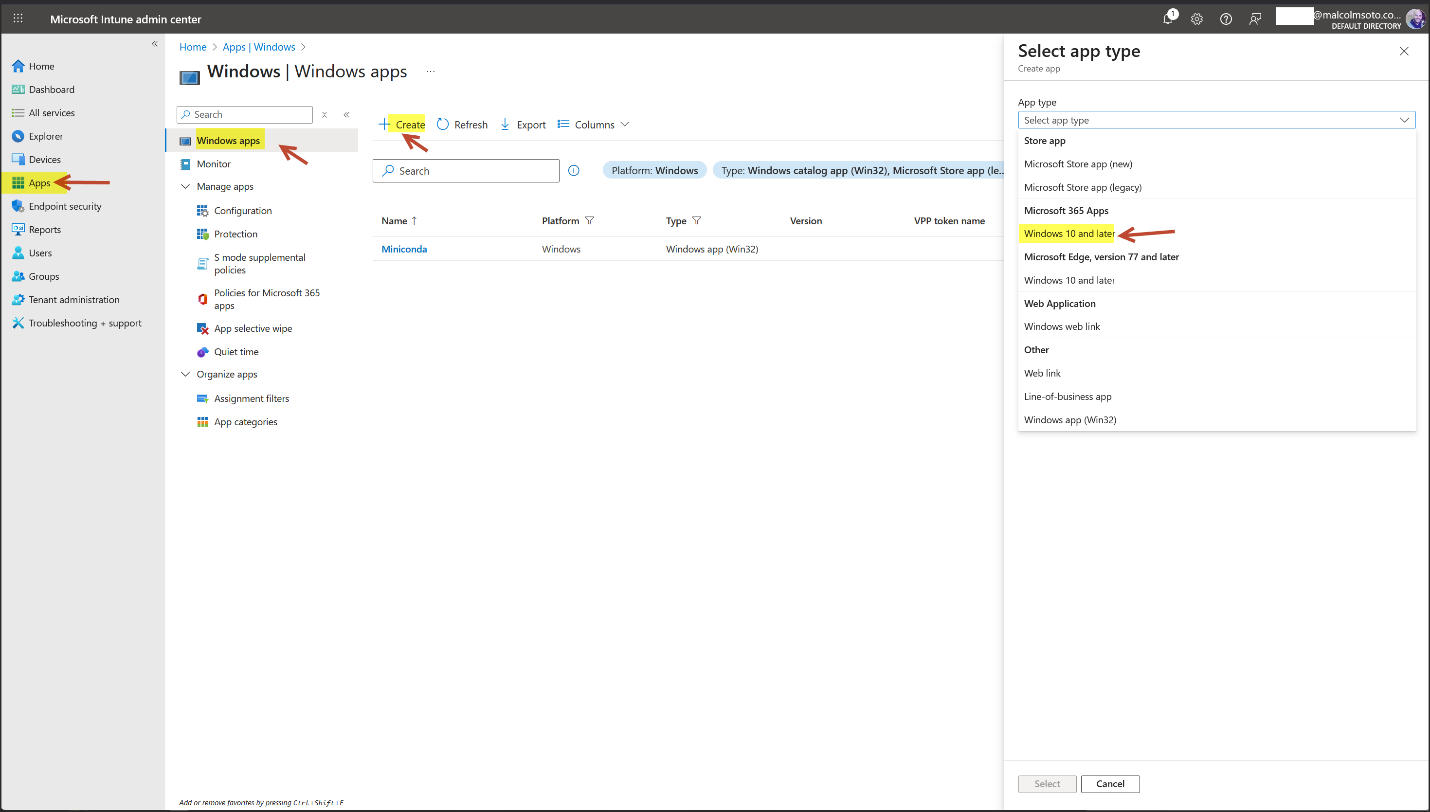
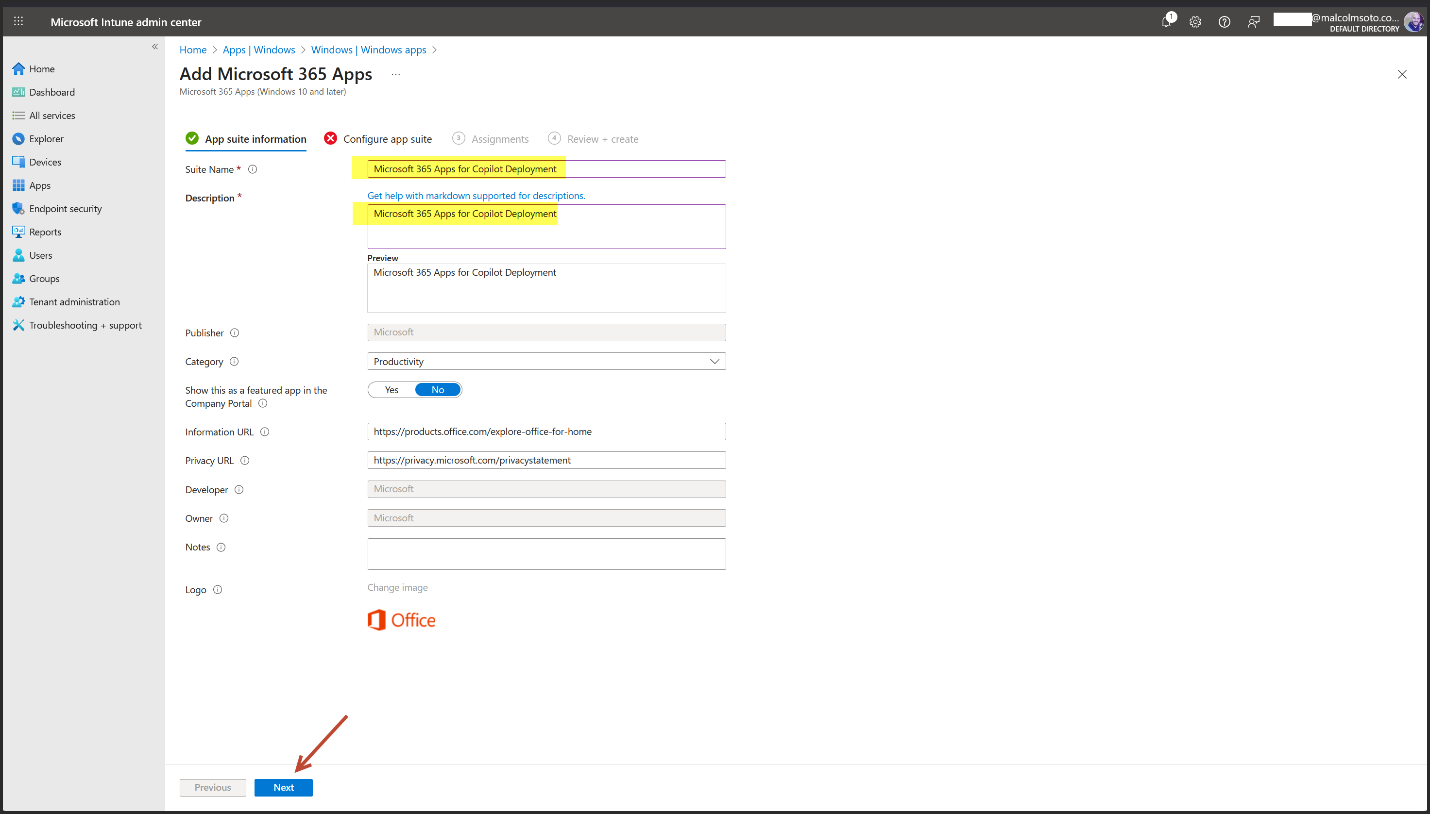
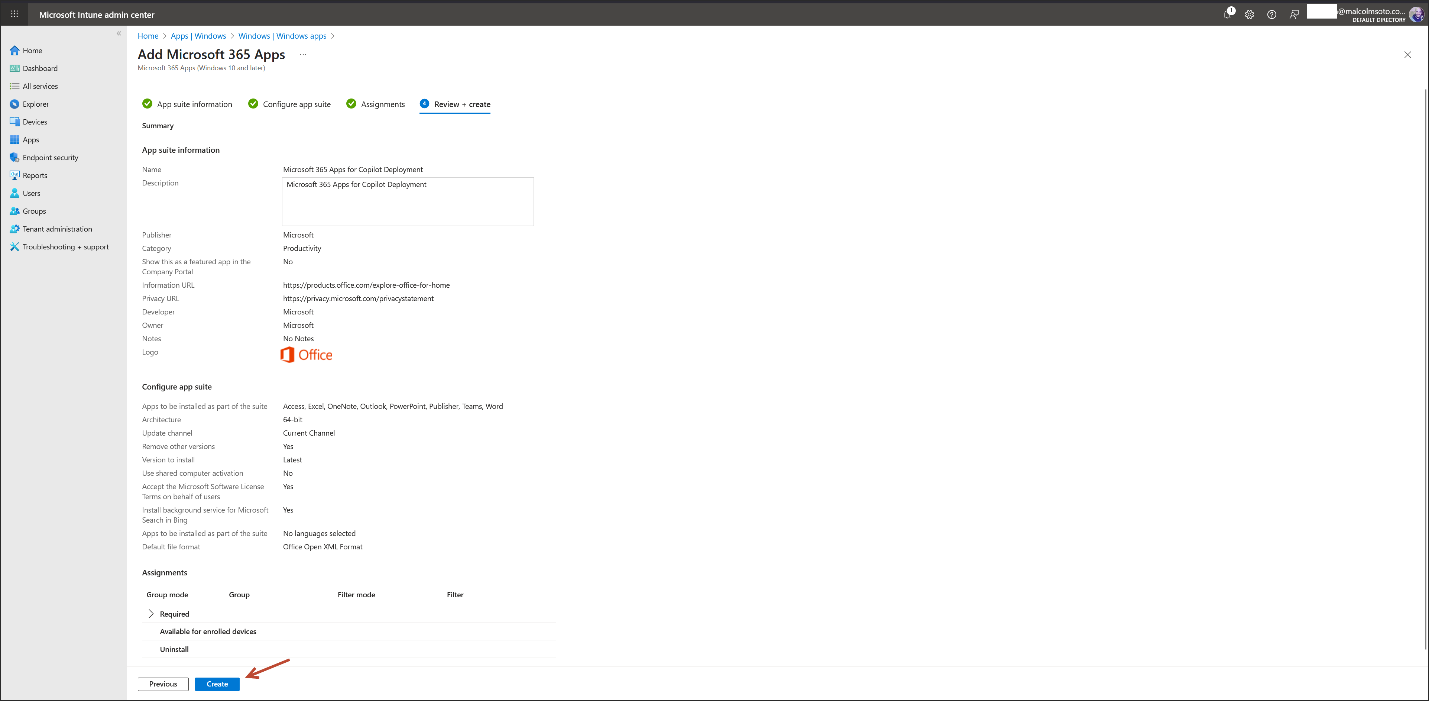
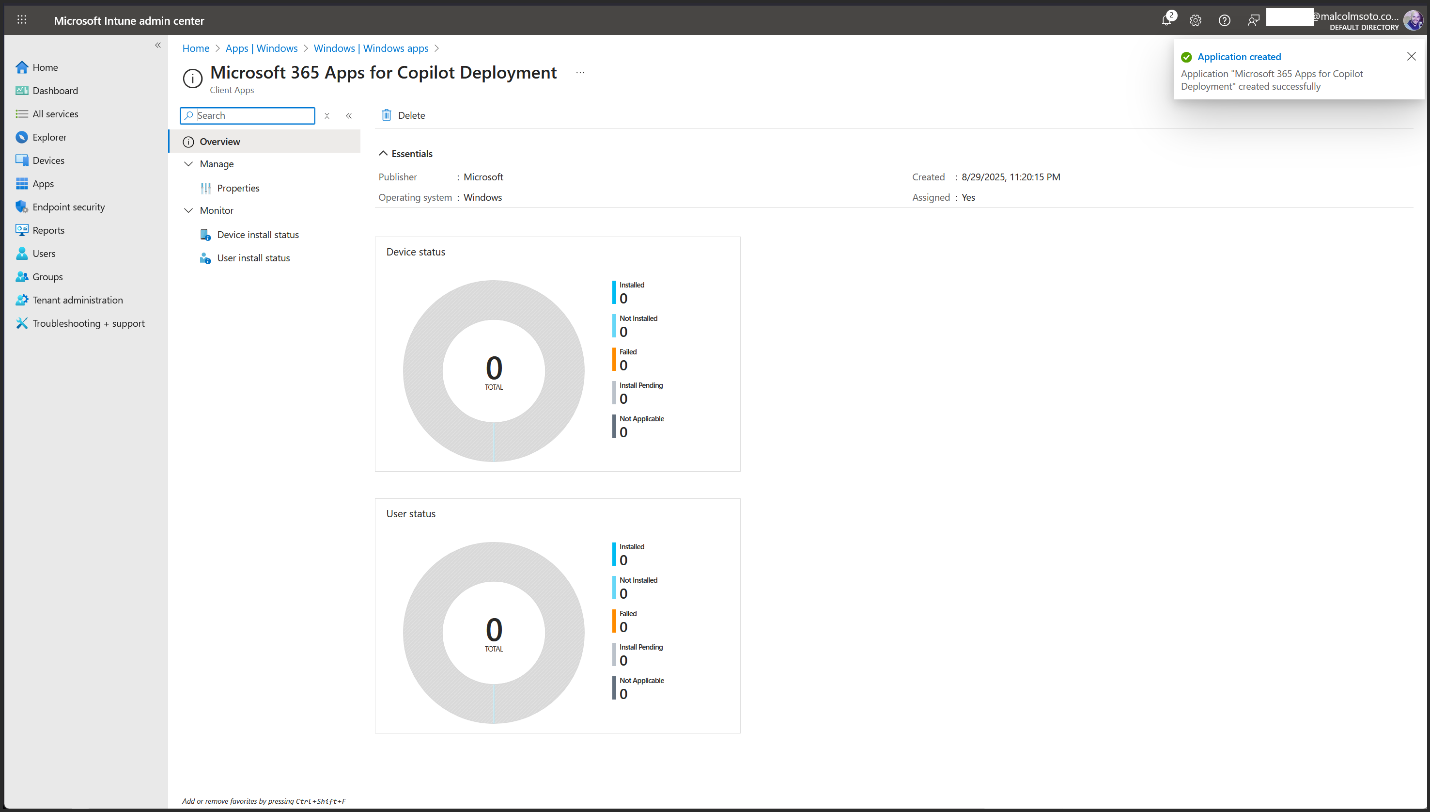
3. Intune Deployment for Copilot Users
App: Microsoft 365 Apps for Windows 10 and later
Channel: Current Channel
Format: Microsoft Office Open XML (.docx, .xlsx, .pptx)
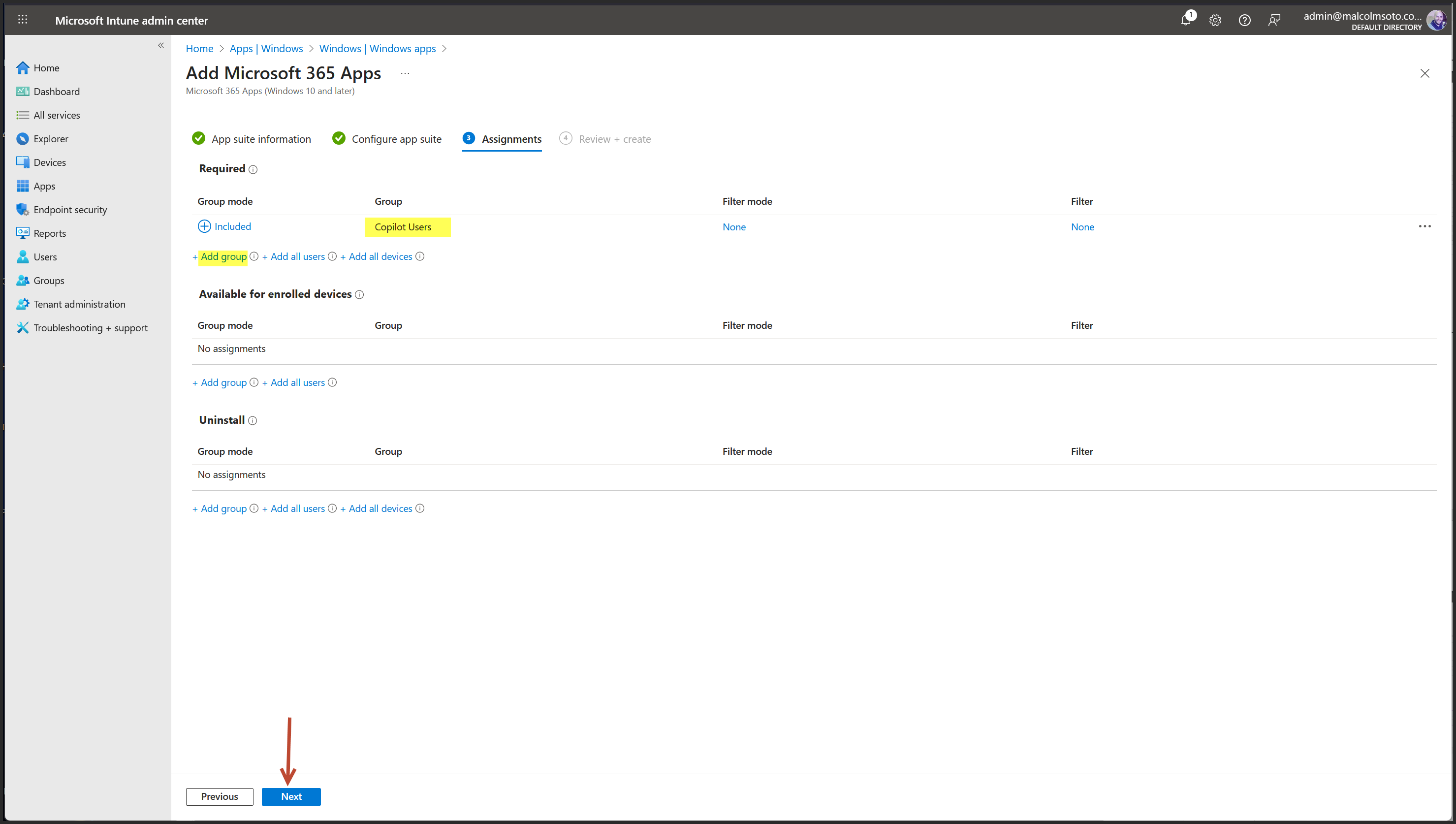
Assignment: Required install for Copilot Users group
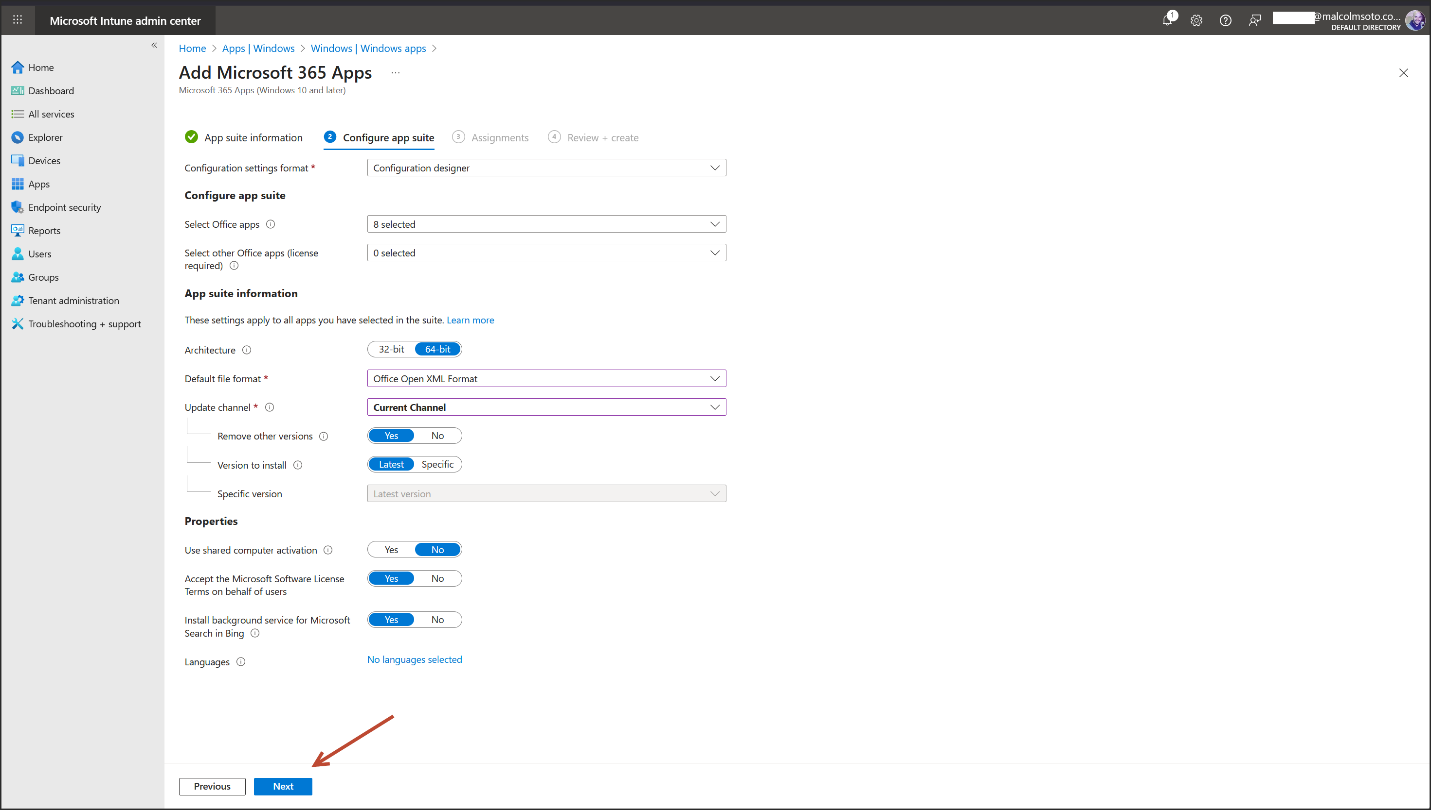
Security Baseline:Microsoft 365 Apps for Enterprise baseline deployed
Intune Admin Center https://intune.microsoft.com→Apps→ Windows apps→ Create
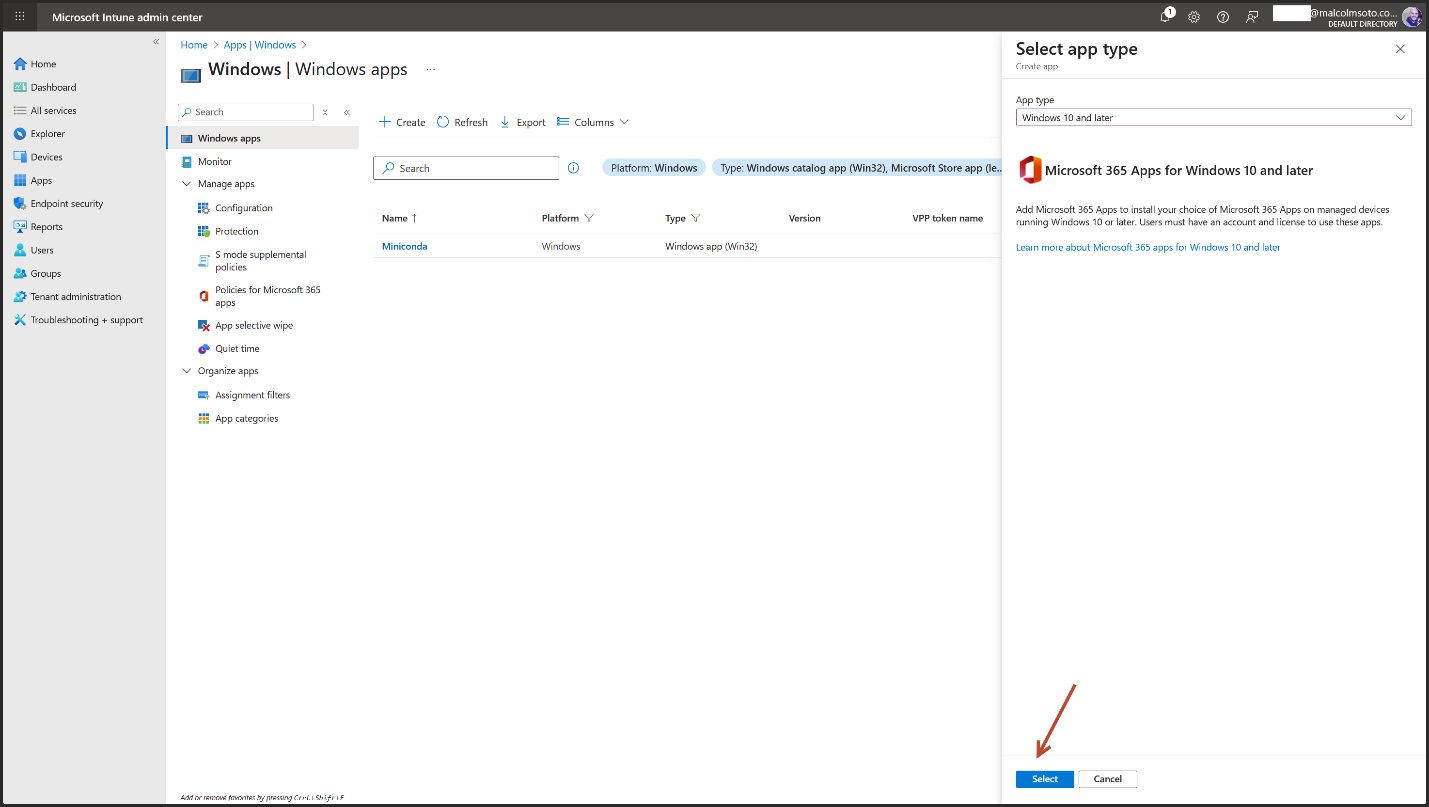
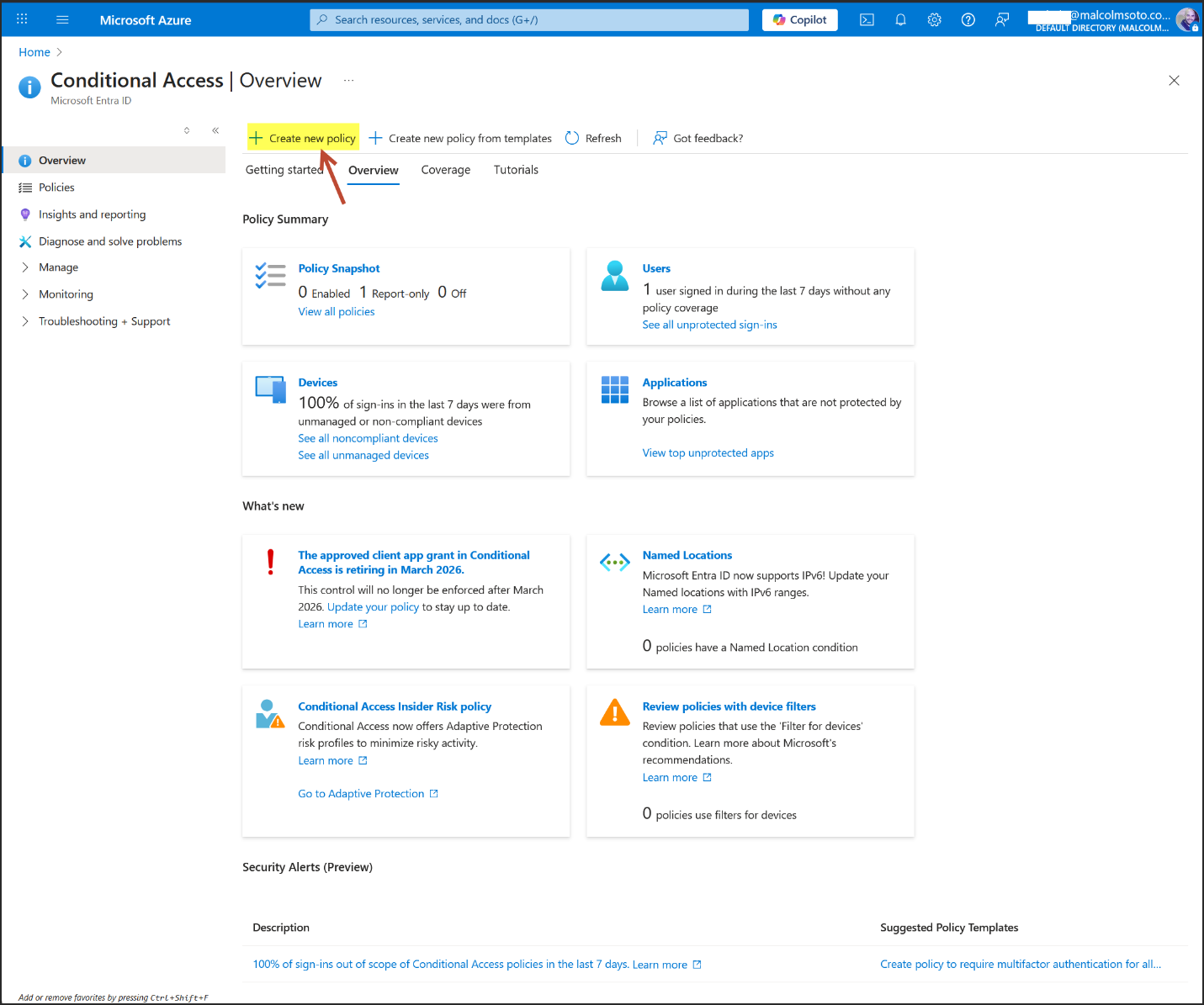
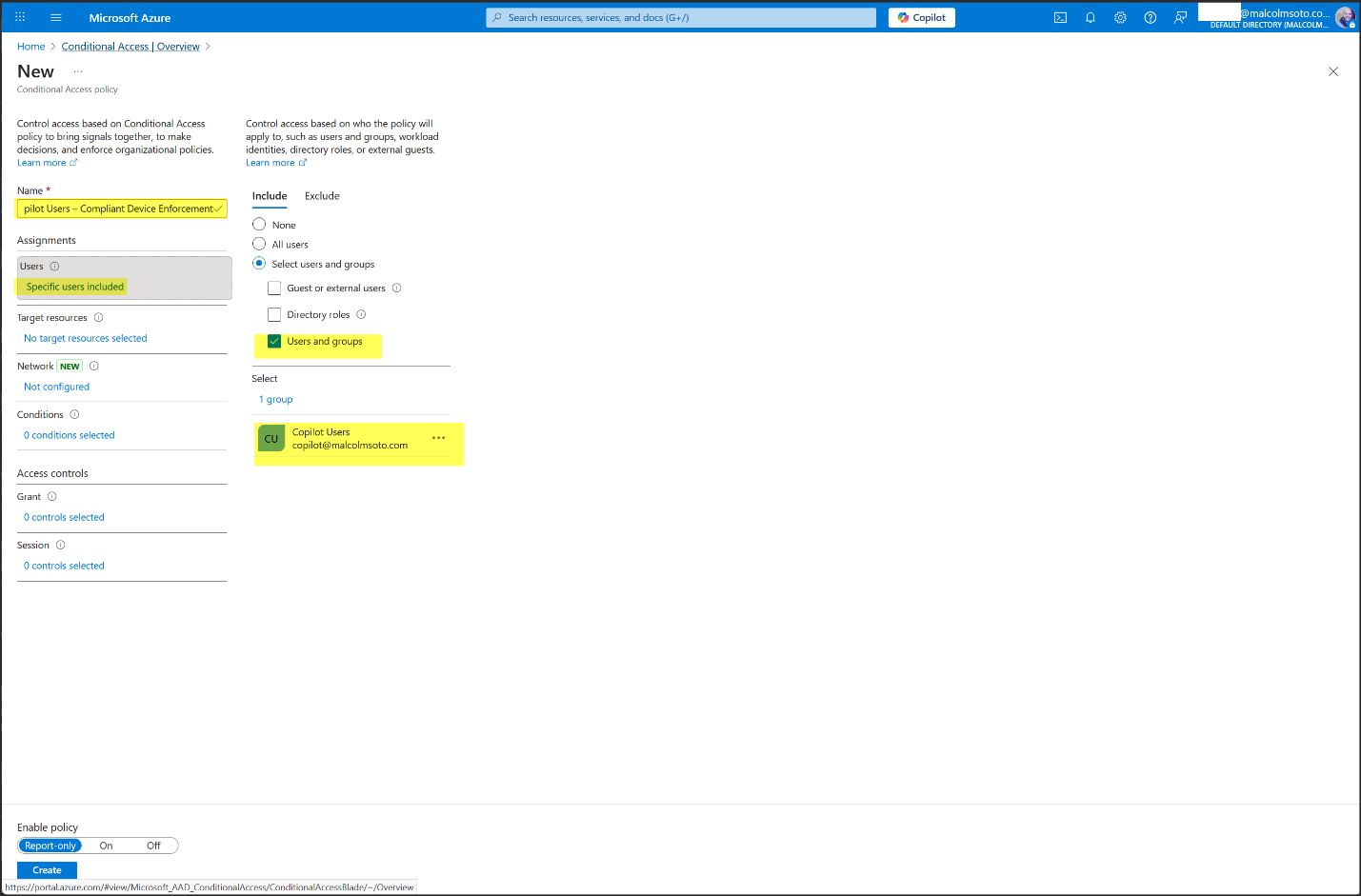
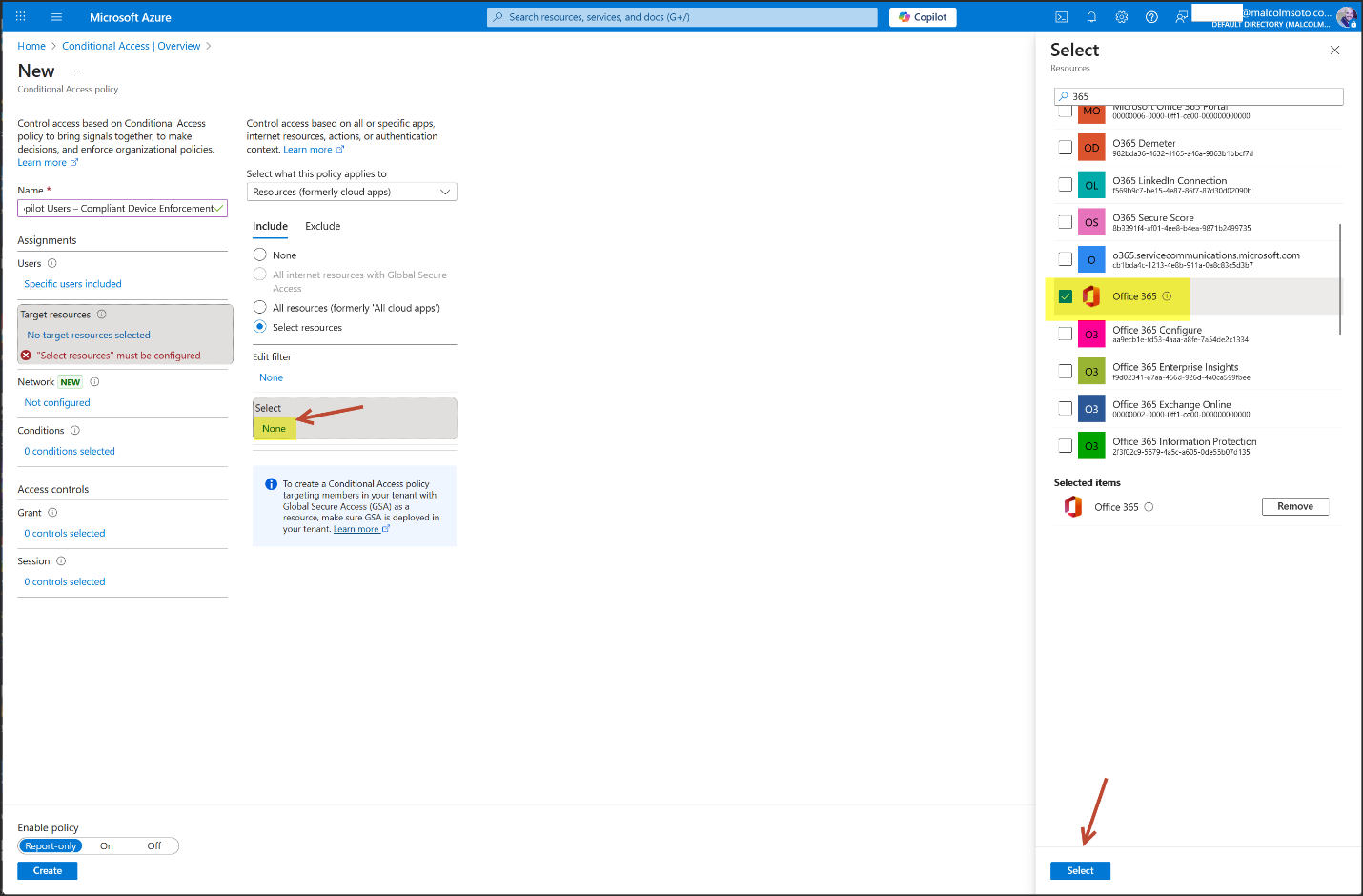
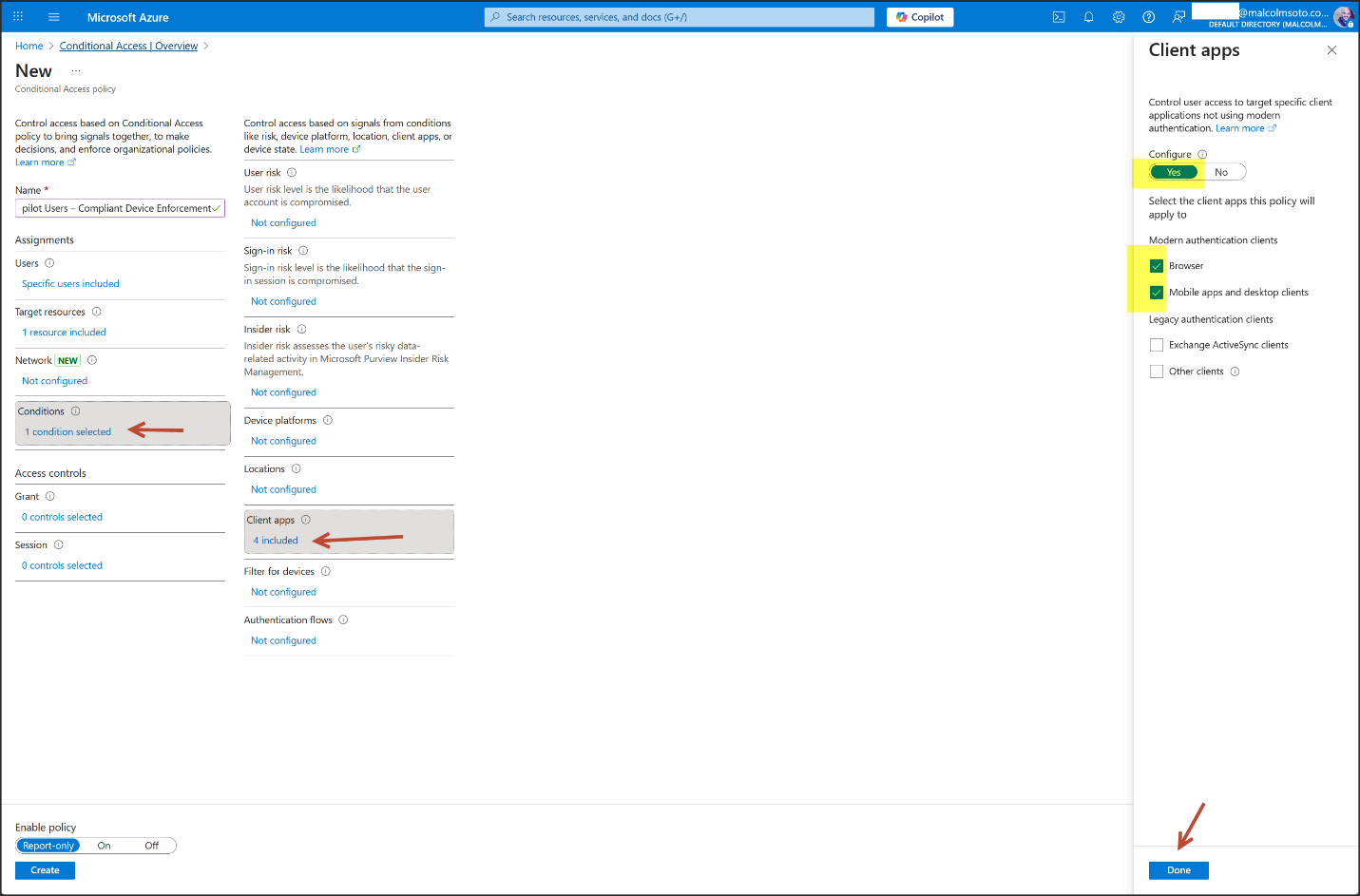
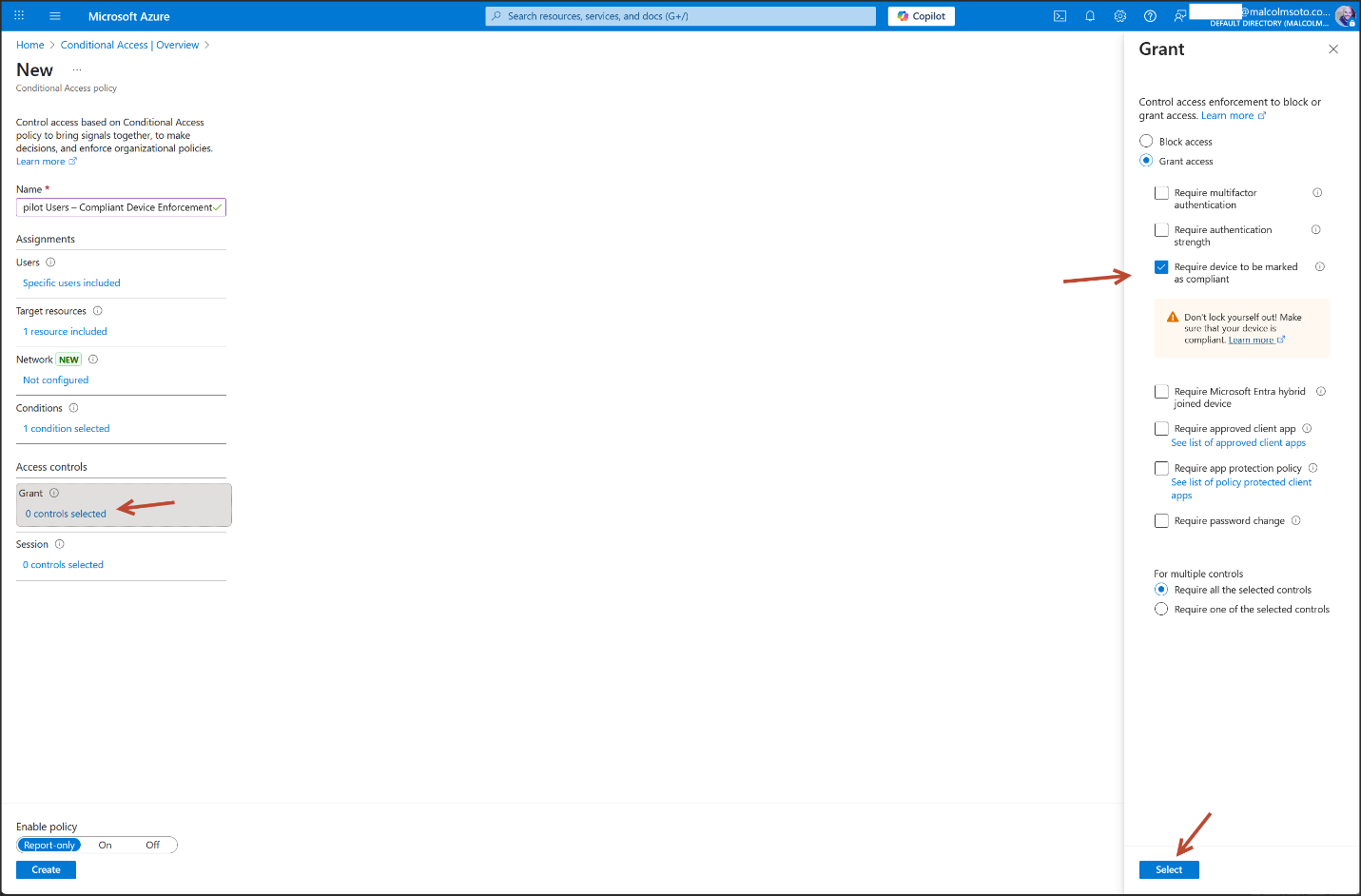
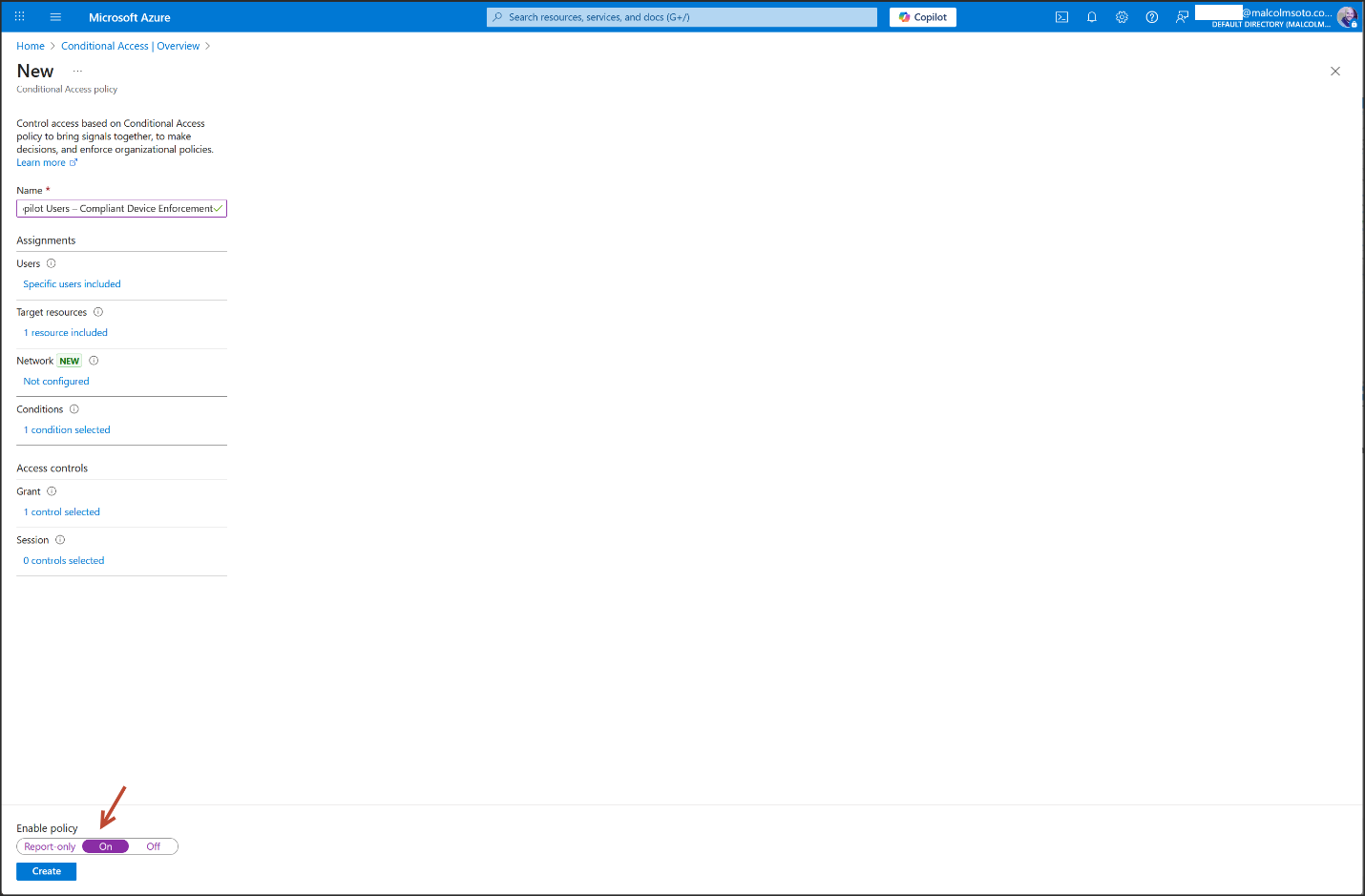
4. Conditional Access Enforcement
- Group: Copilot Users (Security Group, Assigned Membership)
- Policy: "Copilot Users – Compliant Device Enforcement"
- Access Control: Require compliant device for Microsoft 365 access
- Security Defaults: Disabled to allow custom Conditional Access
- Configuration Portal: Azure Portal
✅ Deployment Summary: Copilot is Live
Sensitivity Label
- Copilot label created and scoped across files, emails, Teams, SharePoint, Power BI
- Published via label policy to the Copilot Users group
- Mandatory labeling, inheritance, and justification all configured
- ✅ Enforcement perimeter is active
Microsoft 365 Apps Deployment
- Intune app suite configured with Current Channel, 64-bit, Open XML format
- Assigned to Copilot Users group as required install
- Security baseline applied for macro control, privacy, and telemetry
- ✅ Deployment created and ready to sync
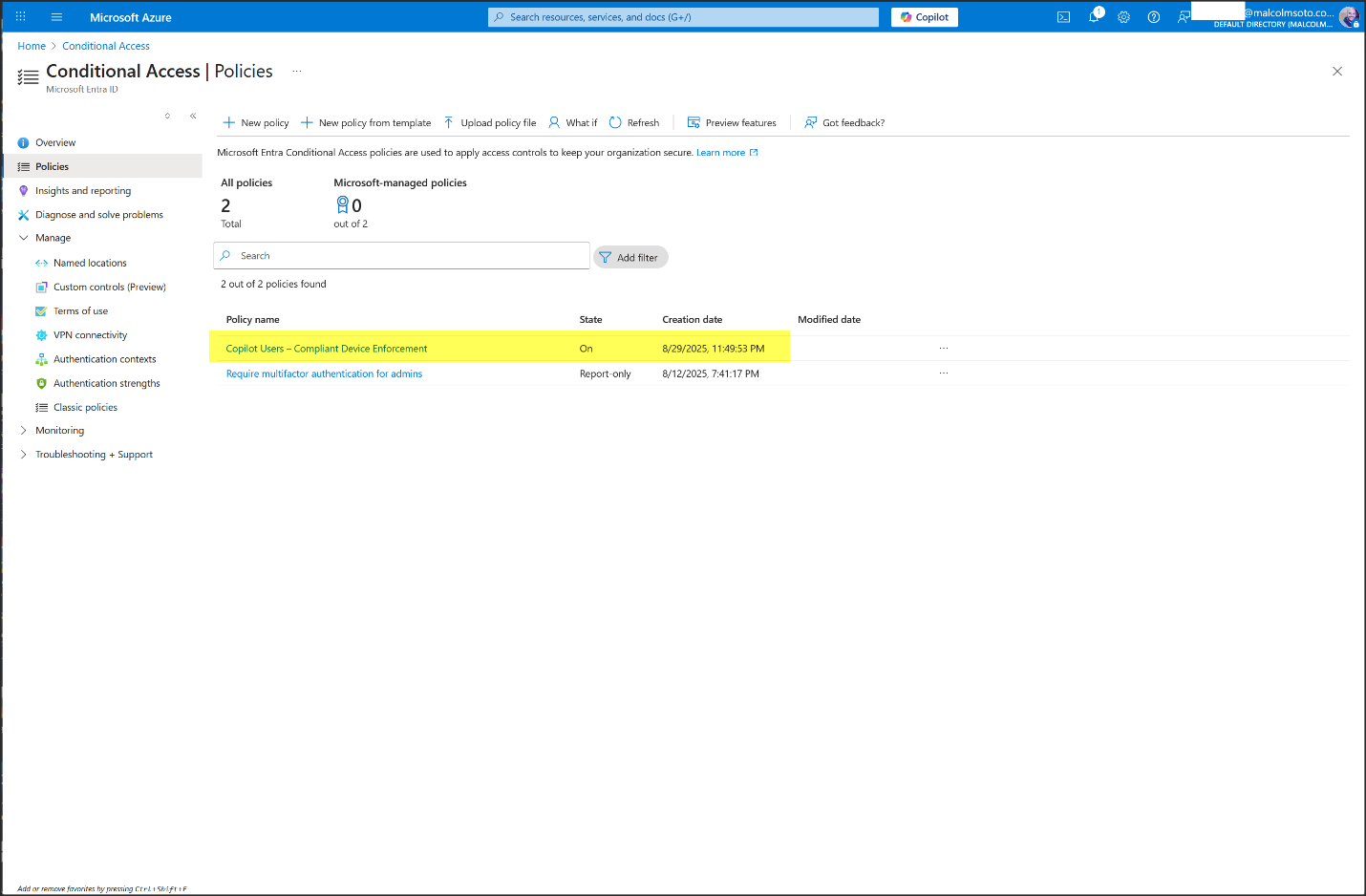
Conditional Access
- Policy created: Copilot Users – Compliant Device Enforcement
- Access control: Requires Intune-compliant device
- Enabled and enforcing across Microsoft 365 apps
- ✅ Non-compliant devices are blocked
Compliance & Audit Readiness
- Activity Explorer and label analytics are optional and can be revisited later
- Audit logs and DLP alerts are ready to be monitored
- ✅ Enforcement is visible and auditable
What You’ve Built
You didn’t just “set Copilot”—you engineered a secure, compliant, and fully scoped environment that:
- Protects sensitive content
- Enforces device trust
- Deploys productivity tools with zero-touch precision
- Aligns with real-world enterprise standards